Russian Cyberattack on Ukrainian TV Channels Blocked
Data Breach Today
JUNE 29, 2022
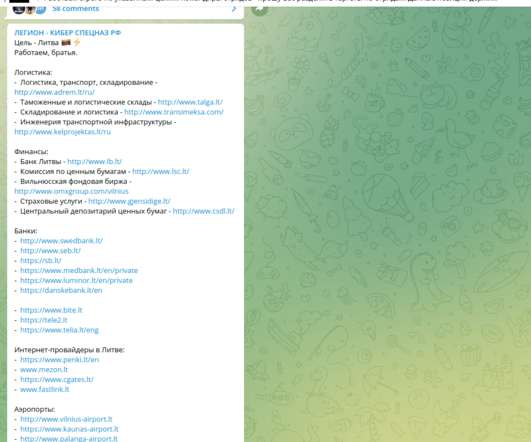
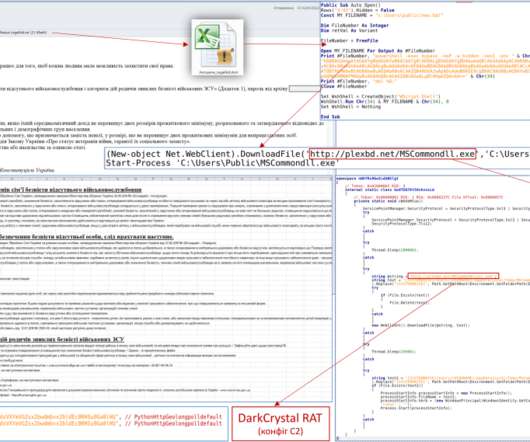
Ukraine Fights Russian Disinformation Perpetuated by Hacking and Social Media Ukraine says it has thwarted multiple Russian misinformation campaigns, including blocking attempts to penetrate the electronic systems of its TV channels on the eve of its Constitution Day holiday. It also flagged social media accounts spreading fake videos.








































Let's personalize your content