Internet Backbone Giant Lumen Shuns.RU
Krebs on Security
MARCH 8, 2022
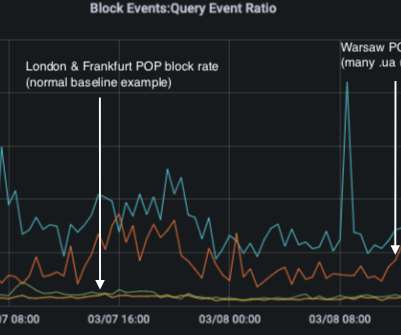
Lumen Technologies , an American company that operates one of the largest Internet backbones and carries a significant percentage of the world’s Internet traffic, said today it will stop routing traffic for organizations based in Russia. Lumen’s decision comes just days after a similar exit by backbone provider Cogent , and amid a news media crackdown in Russia that has already left millions of Russians in the dark about what is really going on with their president’s war in Ukr





































Let's personalize your content