Amazon Sidewalk Raises Privacy and Security Concerns
Data Breach Today
JUNE 3, 2021
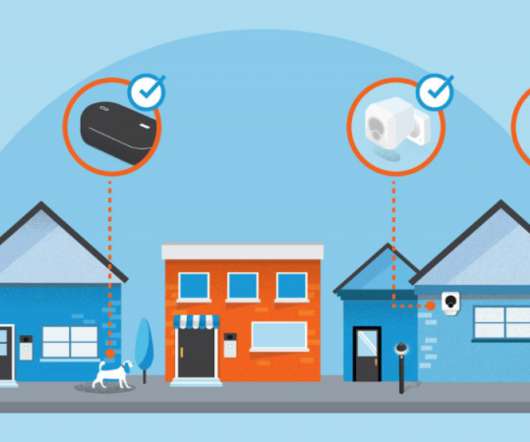
Low-Bandwidth Network Can Share Internet Connections Among Amazon Devices Internet of things security professionals are expressing concern over Amazon's new Sidewalk - a low-bandwidth network program that will allow some of the company's connected and IoT devices to share Wi-Fi access even outside an owner's home.






































Let's personalize your content