Modernization Facts: The Path to Digital Transformation
Micro Focus
JUNE 1, 2020
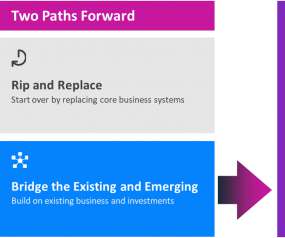
A Changing Normality The worldwide pandemic of 2020 is forcing rapid change for entire organizations—even industries. The ability for organizations to transform into digital-first entities is key to survival. IDC predicts that 60 percent of global GDP will be digitized by 2022. So what does an organization with significant investments in current IT systems do.





































Let's personalize your content