New Android banking Malware targets Brazil’s Itaú Unibanco Bank
Security Affairs
DECEMBER 27, 2021
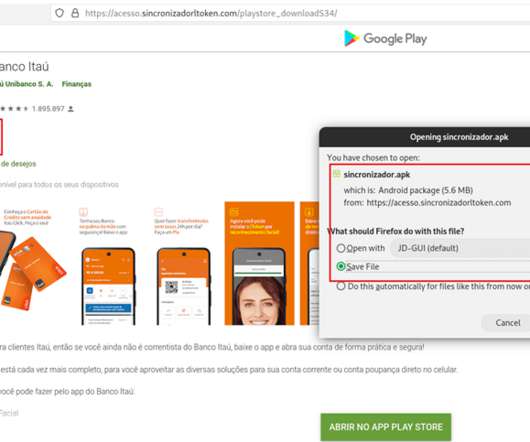
Researchers analyzed a new Android banking malware that targets Brazil’s Itaú Unibanco that spreads through fake Google Play Store pages. Researchers from threat intelligence firm Cyble analyzed a new Android banking malware that targets Brazil’s Itaú Unibanco trying to perform fraudulent financial transactions on the legitimate Itaú Unibanco applications without the victim’s knowledge.





































Let's personalize your content