What Will Cybersecurity's 'New Normal' Look Like?
Dark Reading
JUNE 18, 2020
The coronavirus pandemic has forced changes for much of the business world, cybersecurity included. What can we expect going forward?

Dark Reading
JUNE 18, 2020
The coronavirus pandemic has forced changes for much of the business world, cybersecurity included. What can we expect going forward?

WIRED Threat Level
JUNE 7, 2020
Developers are working on track-and-trace systems to keep infection levels low. The apps aren't here yet, but here's what they do—and how you can enable them.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
JUNE 22, 2020
The so-called BlueLeaks collection includes internal memos, financial records, and more from over 200 state, local, and federal agencies.

Data Breach Today
JUNE 12, 2020
DoppelPaymer Hit Comes as Ransomware Attacks - and Data-Leaking Shakedowns - Surge The attack sounds ripped from an episode of TV show "24": Hackers have infiltrated a government network, and they're days away from unleashing ransomware. Unfortunately for Florence, a city in Alabama, no one saved the day, and officials are sending $300,000 in bitcoins to attackers for a decryption key.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
JUNE 19, 2020
Researchers Find Extensions Could Steal Credentials and Security Tokens Google has removed more than 70 malicious Chrome extensions after researchers with security firm Awake Security discovered the extensions could be used to steal users' credentials and security tokens.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

OpenText Information Management
JUNE 9, 2020
Remote work teams around the world are showing that despite today’s extraordinary circumstances, we can still churn out hearty levels of productivity. But it’s challenging. Maybe it’s our innate desire for connection or our drive to escape social isolation, but lately many of us are missing our teammates and the buzz of an office environment. … The post How to keep your remote work team together appeared first on OpenText Blogs.
Data Breach Today
JUNE 8, 2020
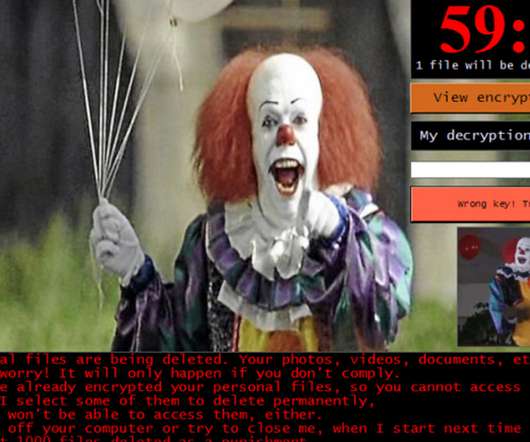
Can't Stop the Crypto-Locking Malware Attacks? Criminals Keep Hitting Big Targets Ransomware gangs continue to innovate: Recently, reports have emerged of collaboration between the Maze and Lockbit gangs, and REvil not just leaking stolen data for free, but auctioning it off to the highest bidder. On the upside, however, security firms continue to release free decryptors for some strains.

Krebs on Security
JUNE 19, 2020
Hundreds of popular websites now offer some form of multi-factor authentication (MFA), which can help users safeguard access to accounts when their password is breached or stolen. But people who don’t take advantage of these added safeguards may find it far more difficult to regain access when their account gets hacked, because increasingly thieves will enable multi-factor options and tie the account to a device they control.

Security Affairs
JUNE 20, 2020
Malicious Chrome browser extensions were employed in a surveillance campaign on a large scale, millions of users potentially impacted. Malicious Chrome browser extensions were used in a massive surveillance campaign aimed at users working in the financial services, oil and gas, media and entertainment, healthcare, government organizations, and pharmaceuticals.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Dark Reading
JUNE 26, 2020
Three ways that security teams can improve processes and collaboration, all while creating the common ground needed to sustain them.

Data Breach Today
JUNE 19, 2020
Creating Cloud-Hosted Attack Infrastructures a Common Practice, Academic Researchers Find Many ethical hackers and other security professionals, such as penetration testers, have weaponized cloud platforms to host online attack infrastructure or have used the platforms to conduct reconnaissance, according security researchers at Texas Tech University.

Data Breach Today
JUNE 15, 2020
Personal Details on 727,000 Accounts in 14 Countries Leaked Delivery Hero, the online food delivery service, has confirmed a data breach of its Foodora brand. Breached information includes personal details for 727,000 accounts - names, addresses, phone numbers, precise location data and hashed passwords - in 14 countries.

The Guardian Data Protection
JUNE 2, 2020
Deal may allow Faculty, linked to senior Tory figures, to analyse social media data, utility bills and credit ratings UK coronavirus updates – live See all our coronavirus coverage An artificial intelligence firm hired to work on the Vote Leave campaign may analyse social media data, utility bills and credit rating scores as part of a £400,000 contract to help the government deal with the coronavirus pandemic.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Krebs on Security
JUNE 21, 2020
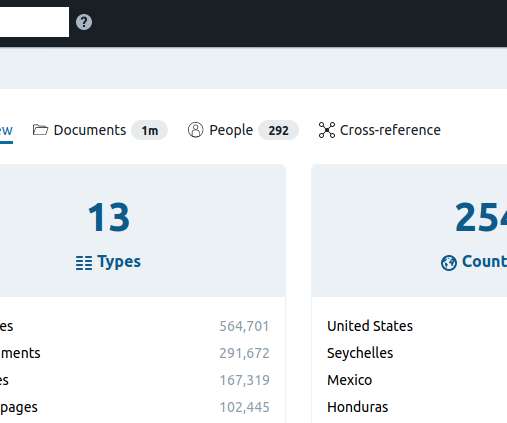
Hundreds of thousands of potentially sensitive files from police departments across the United States were leaked online last week. The collection, dubbed “ BlueLeaks ” and made searchable online, stems from a security breach at a Texas web design and hosting company that maintains a number of state law enforcement data-sharing portals. The collection — nearly 270 gigabytes in total — is the latest release from Distributed Denial of Secrets (DDoSecrets), an alternative to
John Battelle's Searchblog
JUNE 29, 2020
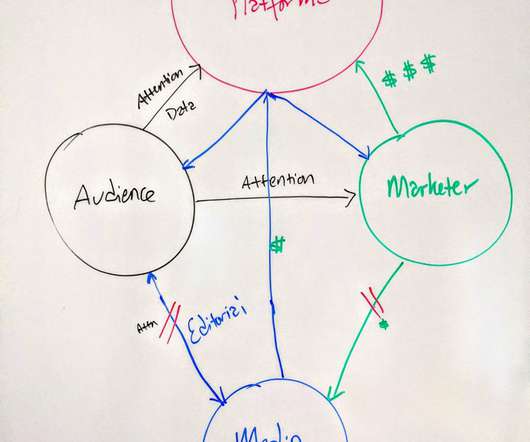
How Brands Can Fix the Relationship Between Platforms, Audiences, and Media Companies (Hint: It’s Not a Boycott). (Second of a series. The first post reviews the media and platform ecosystem, and laments the role brand marketers have played in its demise.) . In my first post of this series, I laid out a fundamental problem with how digital media works today.

Security Affairs
JUNE 26, 2020
A man accused to have developed distributed denial of service (DDoS) botnets based on the Mirai botnet was sentenced to 13 months in federal prison. Kenneth Currin Schuchman, 22, of Vancouver, Washington, was sentenced to 13 months in federal prison because it has developed distributed denial of service (DDoS) botnets based on the source code of Mirai botnet.

IT Governance
JUNE 19, 2020
Cyber criminals have many tricks up their sleeves when it comes to compromising sensitive data. They don’t always rely on system vulnerabilities and sophisticated hacks. They’re just as likely to target the an organisation’s employees. The attack methods they use to do this are known as social engineering. What is social engineering? Social engineering is a collective term for ways in which fraudsters manipulate people into performing certain actions.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Data Breach Today
JUNE 25, 2020
Superseding Indictment Expands Scope of Case, But Doesn't Add Charges The U.S Department of Justice unsealed a superseding indictment against WikiLeaks founder Julian Assange that expands the scope of the government's case against him. Federal prosecutors now allege that Assange conspired with the Anonymous and LulzSec groups to obtain classified information to publish.

The Guardian Data Protection
JUNE 23, 2020
Local health chiefs say real-time information is crucial to monitor spread of disease Coronavirus – latest updates See all our coronavirus coverage Local outbreaks of Covid-19 could grow undetected because the government is failing to share crucial testing data, council leaders and scientists have warned. More than a month after being promised full details of who has caught the disease in their areas, local health chiefs are still desperately lobbying the government’s testing chief, Lady Harding
Krebs on Security
JUNE 9, 2020
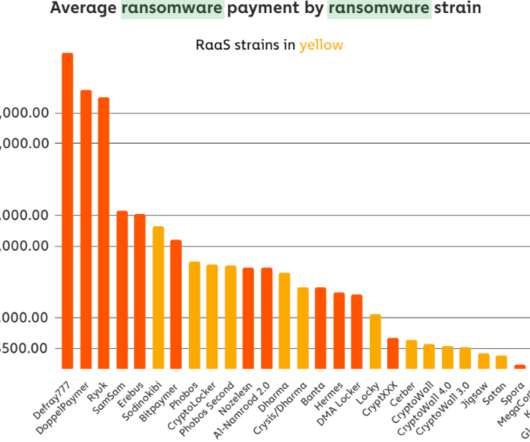
In late May, KrebsOnSecurity alerted numerous officials in Florence, Ala. that their information technology systems had been infiltrated by hackers who specialize in deploying ransomware. Nevertheless, on Friday, June 5, the intruders sprang their attack, deploying ransomware and demanding nearly $300,000 worth of bitcoin. City officials now say they plan to pay the ransom demand, in hopes of keeping the personal data of their citizens off of the Internet.
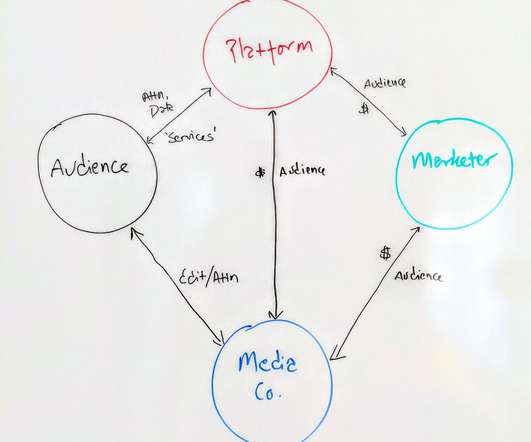
John Battelle's Searchblog
JUNE 17, 2020
It’s getting complicated out there. Marketers – especially brand marketers: Too many of you have lost the script regarding the critical role you play in society. And while well-intentioned TV spots about “getting through this together” are nice, they aren’t a structural solution. It’s time to rethink the relationship between marketers, media companies (not “content creators,” ick), and the audience.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.
Security Affairs
JUNE 28, 2020
Asian media firm E27 suffered a security breach and hackers asked for a “donation” to provide information on the flaws they exploited in the attack. Asian media firm E27 has been hacked by a hacking group identifying themselves as “Korean Hackers” and “Team Johnwick”that asked for a “donation” to provide information on the vulnerabilities they have exploited in the attack.

Jamf
JUNE 11, 2020
Josh Harvey and Allen Golbig of NASA share their Jamf implementation story and explain how organizations can securely provide their employees with the technology they prefer while delivering the best possible user experience.

Data Breach Today
JUNE 23, 2020
New Risks Could Emerge as More Practices Reopen Four recent cybersecurity incidents that may have involved ransomware demonstrate the ongoing threats facing the sector during the COVID-19 pandemic. They also serve as a warning that extra watchfulness is needed as physicians reopen their clinics.
The Guardian Data Protection
JUNE 15, 2020
Smittestopp had limited effect because of the small number of users, says data agency Coronavirus – latest updates See all our coronavirus coverage Norway’s health authorities said they suspended an app designed to help trace the spread of coronavirus after the country’s data protection agency said it was too invasive of privacy. Launched in April, the smartphone app Smittestopp (“infection stop”) was set up to collect movement data to help authorities trace the spread of Covid-19, and inform us

Advertisement
Outdated or absent analytics won’t cut it in today’s data-driven applications – not for your end users, your development team, or your business. That’s what drove the five companies in this e-book to change their approach to analytics. Download this e-book to learn about the unique problems each company faced and how they achieved huge returns beyond expectation by embedding analytics into applications.

Krebs on Security
JUNE 3, 2020
An exhaustive inquiry published today by a consortium of investigative journalists says a three-part series KrebsOnSecurity published in 2015 on a Romanian ATM skimming gang operating in Mexico’s top tourist destinations disrupted their highly profitable business, which raked in an estimated $1.2 billion and enjoyed the protection of top Mexican authorities.

Threatpost
JUNE 5, 2020
A researcher found that phone numbers tied to WhatsApp accounts are indexed publicly on Google Search creating what he claims is a “privacy issue” for users.
Security Affairs
JUNE 21, 2020
Shlayer Mac malware is back, the Mac threat is now spreading through new black SEO operations. Researchers spotted a new version of the Shlayer Mac malware that is spreading via poisoned Google search results. Researchers at security firm Intego observed the new variant being spread masqueraded as a fake Adobe Flash Player installer (.DMG disk image) and implementing fresh advanced evasion capabilities. “The new malware tricks victims into bypassing Apple’s built-in macOS security protecti
Let's personalize your content