Security Lessons We've Learned (So Far) from COVID-19
Dark Reading
MARCH 17, 2020
Takeaways about fighting new fires, securely enabling remote workforces, and human nature during difficult times.

Dark Reading
MARCH 17, 2020
Takeaways about fighting new fires, securely enabling remote workforces, and human nature during difficult times.

Data Breach Today
MARCH 17, 2020
Defense Department to Issue Detailed Security Guidance As more of its employees shift to working from home due to the COVID-19 pandemic, the U.S. Department of Defense is warning workers to take security precautions to guard against potential hackers. It plans to release detailed guidance soon.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
MARCH 20, 2020
US, UK, Other Nations in Talks With Tech Firms to Provide Information The Trump administration is reportedly in talks with tech companies, including Facebook and Google, to explore whether it's possible to use real-time location data from smartphones to support efforts to slow the spread of COVID-19. But some privacy advocates are raising concerns about such tracking efforts.

Dark Reading
MARCH 13, 2020
While there's a ton of unbounded optimism from vendor marketing and consultant types, practitioners are still reserving a lot of judgment.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Data Breach Today
MARCH 17, 2020
Experts: This Week's 'Black Monday' Likely to Accelerate Security M&A Activity With U.S. stock markets suffering their worst day since 1987 on Monday, most technology firms took a hit as Wall Street continues to be rattled by the COVID-19 crisis. Experts predict this will drive fresh waves of consolidation and M&A in the cybersecurity market, as well as growth in hot areas.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

IBM Big Data Hub
MARCH 20, 2020
We recognize that these are difficult times. In response to the worldwide pandemic, IBM will be extending the SPSS Statistics Subscription trial for active and new accounts through June 15. This will allow our users time to adjust to this dynamic and unprecedented situation.

erwin
MARCH 19, 2020
An enterprise architecture framework is a standardized methodology that organizations use to create, describe and change their enterprise architectures. Enterprise architecture (EA) itself describes the blueprint and structure of an organization’s systems and assets. It’s needed to make informed changes that help bridge the gap between the enterprise architecture’s current and desired future state.

IT Governance
MARCH 2, 2020
At first glance, February appears to be a big improvement cyber security-wise compared to the start of the year. The 632,595,960 breached records accounts for about a third of January’s total, and is considerably lower than the figures for this time last year. Unfortunately, the number of breached records doesn’t tell the full story, as there were a whopping 105 incidents – making February 2020 the second leakiest month we’ve ever recorded.

Security Affairs
MARCH 10, 2020
Today Microsoft accidentally leaked info about a new wormable vulnerability (CVE-2020-0796) in the Microsoft Server Message Block (SMB) protocol. Today Microsoft accidentally leaked info on a security update for a wormable vulnerability in the Microsoft Server Message Block (SMB) protocol. The issue, tracked as CVE-2020-0796 , is pre- remote code execution vulnerability that resides in the Server Message Block 3.0 (SMBv3) network communication protocol, the IT giant will not address the issue a

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Data Breach Today
MARCH 23, 2020
Latest Schemes Target At-Home Employees; Some Spoof Health Agencies As the global COVID-19 pandemic worsens, security firms and law enforcement, including the FBI, are warning of increasing phishing and other the cybercriminal scams targeting a largely at-home workforce.

Krebs on Security
MARCH 17, 2020
With many people being laid off or working from home thanks to the Coronavirus pandemic, cybercrooks are almost certain to have more than their usual share of recruitable “ money mules ” — people who get roped into money laundering schemes under the pretense of a work-at-home job offer. Here’s the story of one upstart mule factory that spoofs a major nonprofit and tells new employees they’ll be collecting and transmitting donations for an international “Corona

Troy Hunt
MARCH 12, 2020
I hate dodgy WiFi, hate it with a passion. I finally lost my mind with it a few years ago now so I went and shelled out good money on the full suite of good Ubiquiti gear. I bought a security gateway to do DHCP, a couple of switches for all my connected things, 5 access points for my wireless things and a Cloud Key to control them all. I went overboard and I don't regret it one bit!

erwin
MARCH 12, 2020
Almost 70 percent of CEOs say they expect their companies to change their business models in the next three years, and 62 percent report they have management initiatives or transformation programs underway to make their businesses more digital, according to Gartner. Wouldn’t it be advantageous for these organizations to accelerate these digital transformation efforts?

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

The Guardian Data Protection
MARCH 7, 2020
Vanessa Teague reported on a dataset of Medicare and PBS payments that was supposed to be anonymous but wasn’t A prominent university professor has quit after the health department pressured her university to stop her speaking out about the Medicare and PBS history of over 2.5 million Australians being re-identifiable online due to a government bungle.

Micro Focus
MARCH 3, 2020
“How do I know what I do not know?” Micro Focus IDOL (Intelligent Data Operating Layer) is an AI platform which derives contextual and conceptual insights from miltiple data sources. It can identify relationships that exist within virtually any type of information and Micro Focus runs a demo environment that indexes a limited subset of. View Article.

Data Breach Today
MARCH 30, 2020
Privacy Gaffe Blamed on Facebook's iOS Software Development Kit Zoom has apologized for sharing large sets of user data by default with Facebook, blaming the social network's software development kit, which it has removed from its iOS app. With COVID-19 driving unprecedented levels of remote working, video conferencing software is under the privacy and security microscope.
Krebs on Security
MARCH 10, 2020
FBI officials last week arrested a Russian computer security researcher on suspicion of operating deer.io , a vast marketplace for buying and selling stolen account credentials for thousands of popular online services and stores. Kirill V. Firsov was arrested Mar. 7 after arriving at New York’s John F. Kennedy Airport, according to court documents unsealed Monday.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Thales Cloud Protection & Licensing
MARCH 19, 2020
The need to ensure the ability to work from anywhere is more important than ever. In today’s business environment, constant access to information and services is essential for communication and getting business done whether you are in sales, finance, marketing or the legal profession. This is especially true when we face global incidents like we face today.
erwin
MARCH 17, 2020
Because of the coronavirus pandemic, organizations across the globe are changing how they operate. Teams need to urgently respond to everything from massive changes in workforce access and management to what-if planning for a variety of grim scenarios, in addition to building and documenting new applications and providing fast, accurate access to data for smart decision-making.

Security Affairs
MARCH 16, 2020
While the Coronavirus is spreading in the U.S., a mysterious cyberattack hit the Department of Health and Human Services on Saturday. According to Bloomberg, that cited three people familiar with the matter, a cyberattack hit the U.S. Department of Health and Human Services on Saturday night. People cited by Bloomberg confirmed that the cyber attack aimed at slowing the agency’s systems down. “The U.S.

OpenText Information Management
MARCH 31, 2020
All the major examples of supply chain disruptions over the previous 20 years – from the SARS epidemic to the Fukushima earthquake and tsunami – have led to the development of new levels of supply chain risk management. However, the lessons learned about the vulnerabilities in global supply chains from these events can’t easily be … The post How to adapt to supply chain disruptions caused by the Coronavirus appeared first on OpenText Blogs.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

Data Breach Today
MARCH 12, 2020
SecuredTouch CEO Alasdair Rambaud on 2020 Innovations Behavioral biometrics is seeing wide adoption and is helping organizations proactively fight fraud, says Alasdair Rambaud, CEO at SecuredTouch. who describes the latest innovations.
Krebs on Security
MARCH 20, 2020
Finastra , a company that provides a range of technology solutions to banks worldwide, said it was shutting down key systems in response to a security breach discovered Friday morning. The company’s public statement and notice to customers does not mention the cause of the outage, but their response so far is straight out of the playbook for dealing with ransomware attacks.

Thales Cloud Protection & Licensing
MARCH 6, 2020
Disconnecting from your mobile device, laptop or tablet can be as good as a holiday. Simply taking a pause from email and social media in favor of a good book or conversation is known to increase your mood and life satisfaction. But it’s also a chance to step back and re-evaluate our online usage. In my family, we regularly ‘unplug’ and use the opportunity to discuss cyber awareness and topics such as the risks to our family information, how we can improve personal safety, and what are we doing

erwin
MARCH 5, 2020
The value of enterprise architecture to innovation management and digital transformation is clear. Innovation management is about quickly and effectively implementing your organization’s goals through the adoption of innovative ideas, products, processes and business models. Most organizations are beginning to realize that to drive business growth and maintain a competitive advantage, innovation needs to be uncovered, documented and socialized rapidly but with care to ensure maximum value.

Advertisement
Outdated or absent analytics won’t cut it in today’s data-driven applications – not for your end users, your development team, or your business. That’s what drove the five companies in this e-book to change their approach to analytics. Download this e-book to learn about the unique problems each company faced and how they achieved huge returns beyond expectation by embedding analytics into applications.
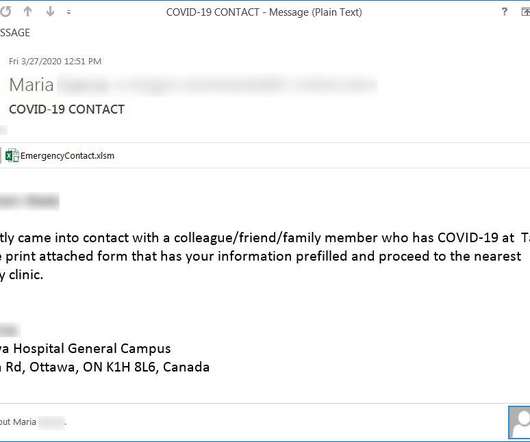
Security Affairs
MARCH 30, 2020
Security experts uncovered a new Coronavirus-themed phishing campaign, the messages inform recipients that they have been exposed to the virus. Experts continue to spot Coronavirus-themed attack, a new phishing campaign uses messages that pretend to be from a local hospital informing the victims they have been exposed to the virus and that they need urgently to be tested.
HL Chronicle of Data Protection
MARCH 16, 2020
Data protection authorities from around the world are stepping in to provide their input and guidance on the matter of data processing activities and the fight against the coronavirus. Hogan Lovells’ global Privacy and Cybersecurity team has compiled the guidance from various European authorities, which is available here. The different emphasis among the data protection authorities’ views – which can be categorized as restrictive, neutral or permissible – suggests that the right approach must l
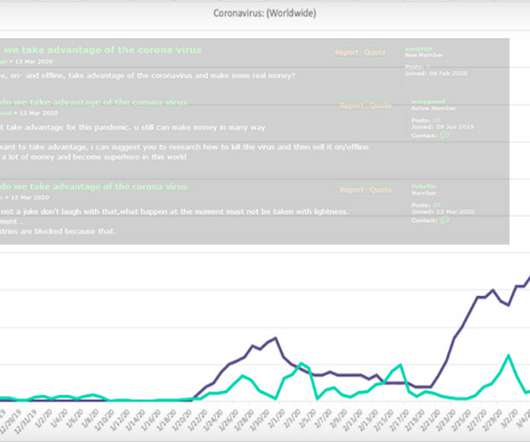
Data Breach Today
MARCH 20, 2020
Businesses Asked to Report COVID-19-Themed Crime to Police As cybercriminals and nation-states take advantage of the COVID-19 pandemic to further their own aims, authorities are calling on victims to report online attacks as quickly as possible to help them better disrupt such activity.
Let's personalize your content