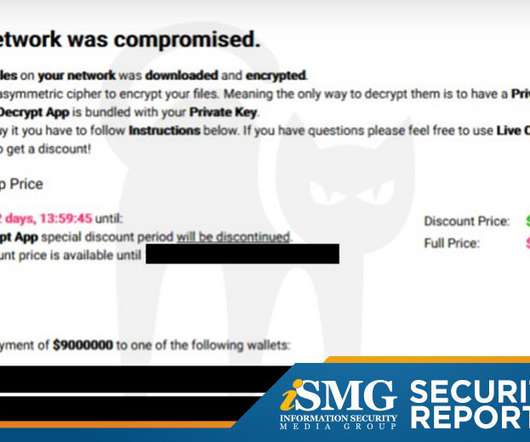
Why Are Ransomware Attacks Intensifying?
Data Breach Today
JULY 14, 2022
The latest edition of the ISMG Security Report analyzes why the number of ransomware attacks and the amounts being paid in ransoms are both on the rise. It also discusses today's cyberthreat landscape and whether organizations should rely on user training to improve security.





































Let's personalize your content