Hoax Email Blast Abused Poor Coding in FBI Website
Krebs on Security
NOVEMBER 13, 2021
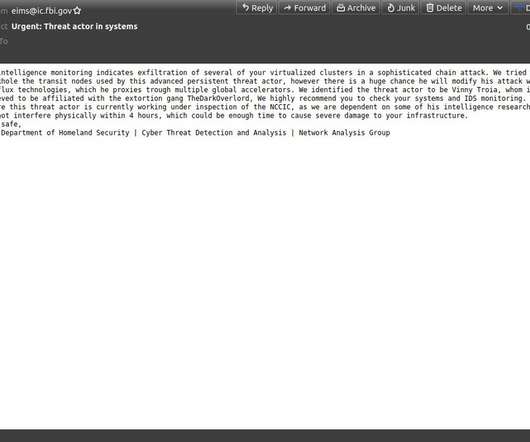
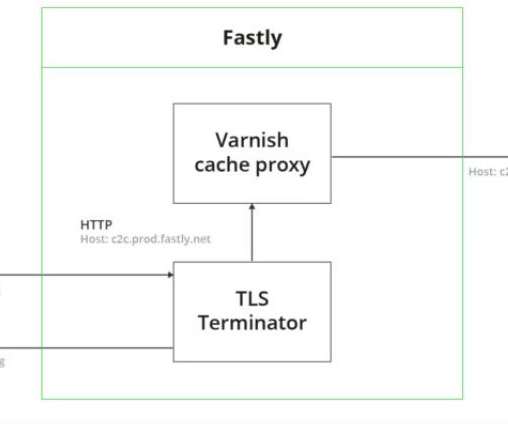
The Federal Bureau of Investigation (FBI) confirmed today that its fbi.gov domain name and Internet address were used to blast out thousands of fake emails about a cybercrime investigation. According to an interview with the person who claimed responsibility for the hoax, the spam messages were sent by abusing insecure code in an FBI online portal designed to share information with state and local law enforcement authorities.






































Let's personalize your content