‘Trojan Source’ Bug Threatens the Security of All Code
Krebs on Security
OCTOBER 31, 2021
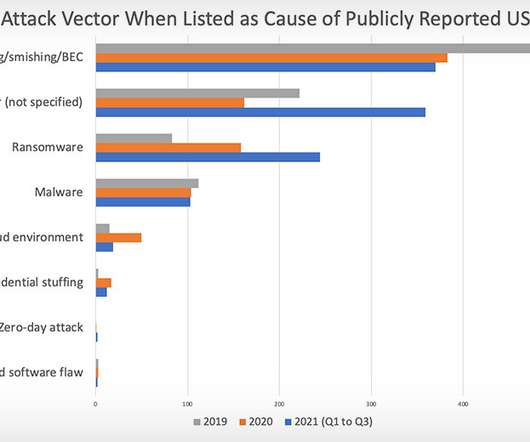
Virtually all compilers — programs that transform human-readable source code into computer-executable machine code — are vulnerable to an insidious attack in which an adversary can introduce targeted vulnerabilities into any software without being detected, new research released today warns. The vulnerability disclosure was coordinated with multiple organizations, some of whom are now releasing updates to address the security weakness.

































Let's personalize your content