FBI, CISA Warn of Election Results Disinformation Campaigns
Data Breach Today
SEPTEMBER 23, 2020
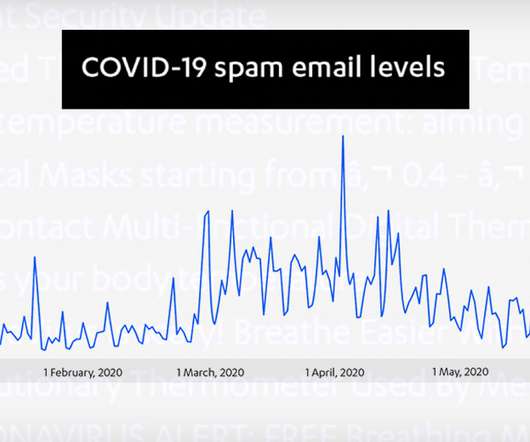
Nation-States, Others Could Try to Undermine Confidence in Election Process With less than 45 days to go before the November election, the FBI and CISA have issued a warning that nation-state hackers and cybercriminals may attempt to spread disinformation regarding the final vote tallies as a way to undermine confidence in the voting process.





































Let's personalize your content