7 Steps to Take Right Now to Prepare for Cyberattacks by Russia
Dark Reading
FEBRUARY 25, 2022
A lot of the recommended preparation involves measures organizations should have in place already.

Dark Reading
FEBRUARY 25, 2022
A lot of the recommended preparation involves measures organizations should have in place already.

Krebs on Security
FEBRUARY 3, 2022
If you received a link to LinkedIn.com via email, SMS or instant message, would you click it? Spammers, phishers and other ne’er-do-wells are hoping you will, because they’ve long taken advantage of a marketing feature on the business networking site which lets them create a LinkedIn.com link that bounces your browser to other websites, such as phishing pages that mimic top online brands (but chiefly Linkedin’s parent firm Microsoft ).
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
FEBRUARY 28, 2022
One could make the argument that Application Programming Interfaces — APIs – are a vital cornerstone of digital transformation. Related: How a dynamic WAF can help protect SMBs. APIs interconnect the underlying components of modern digital services in a very flexible, open way. This has resulted in astounding innovations in cloud services, mobile computing, IoT systems and agile software development.

Jamf
FEBRUARY 11, 2022
The remediation for a serious security vulnerability in Microsoft Active Directory (AD) prevents Apple macOS from binding. Affected machines will lose the ability to communicate with AD domain controllers, resulting in user lockout and potential data loss.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Security Affairs
FEBRUARY 17, 2022
Attackers compromise Microsoft Teams accounts to attach malicious executables to chat and spread them to participants in the conversation. While the popularity of Microsoft Teams continues to grow, with roughly 270 million monthly active users , threat actors started using it as an attack vector. Starting in January 2022, security researchers from Avanan observed attackers compromising Microsoft Teams accounts attach malicious executables to chat and infect participants in the conversation.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Schneier on Security
FEBRUARY 9, 2022
Researchers have calculated the quantum computer size necessary to break 256-bit elliptic curve public-key cryptography: Finally, we calculate the number of physical qubits required to break the 256-bit elliptic curve encryption of keys in the Bitcoin network within the small available time frame in which it would actually pose a threat to do so. It would require 317 × 10 6 physical qubits to break the encryption within one hour using the surface code, a code cycle time of 1 μ s, a reaction

Krebs on Security
FEBRUARY 22, 2022
Missouri Governor Mike Parson made headlines last year when he vowed to criminally prosecute a journalist for reporting a security flaw in a state website that exposed personal information of more than 100,000 teachers. But Missouri prosecutors now say they will not pursue charges following revelations that the data had been exposed since 2011 — two years after responsibility for securing the state’s IT systems was centralized within Parson’s own Office of Administration.

Hunton Privacy
FEBRUARY 7, 2022
On January 24, 2022, a group of state attorneys general (Indiana, Texas, D.C. and Washington) (the “State AGs”) announced their commitment to ramp up enforcement work on “dark patterns” that are used to ascertain consumers’ location data. The State AGs created a plan to initiate lawsuits alleging that consumers of certain online services are falsely led to believe that they can prevent the collection of their location data by changing their account and device settings, when the online services d

Jamf
FEBRUARY 15, 2022
Learn how the partnership between Jamf Pro and Google BeyondCorp enables you to construct a compliance and security framework around end-user devices, blending Jamf’s device management with Google’s endpoint management security for a comprehensive, cloud-based, Zero Trust solution.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Security Affairs
FEBRUARY 19, 2022
The U.S. CISA has created a list of free cybersecurity tools and services that can help organizations increase their resilience. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced this week that it has compiled a list of free cybersecurity tools and services that can help organizations to reduce cybersecurity risk and increase resilience.
IT Governance
FEBRUARY 22, 2022
Information security management is a way of protecting an organisation’s sensitive data from threats and vulnerabilities. The process is typically embedded via an ISMS (information security management system) , which provides the framework for managing information security. At the centre of the framework is information risk management in, which organisations assess risks and the ways that they can compromise the confidentiality, integrity and availability of information.

WIRED Threat Level
FEBRUARY 2, 2022
Disappointed with the lack of US response to the Hermit Kingdom's attacks against US security researchers, one hacker took matters into his own hands.
eSecurity Planet
FEBRUARY 11, 2022
Machine learning (ML) and artificial intelligence (AI) have emerged as critical tools for dealing with the ever-growing volume and complexity of cybersecurity threats. Machines can recognize patterns to detect malware and unusual activity better than humans and classic software. The technology also predicts potential attacks and automatically responds to threats by identifying specific trends and cycles.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Hunton Privacy
FEBRUARY 24, 2022
On February 23, 2022, the European Commission adopted a Proposal for a Regulation designed to harmonize rules on the fair access to and use of data generated in the EU across all economic sectors (the “Data Act”). The Data Act is intended to “ensure fairness in the digital environment, stimulate a competitive data market, open opportunities for data-driven innovation and make data more accessible for all.

Data Protection Report
FEBRUARY 14, 2022
Recent decisions out of the EU will impact the use of Google Analytics and similar non-European analytics services when targeting EU individuals, with the potential to put many organizations at risk of receiving GDPR fines. At issue was the transfer of personal data from the EU to the US through the use of Google Analytics. These decisions, like the Schrems decisions, make it clear that organizations must have a technical understanding of their data flows, with an emphasis on: (1) where the data
Security Affairs
FEBRUARY 28, 2022
Anonymous and other hacker groups that responded to the call to war against Russia continue to launch cyberattacks on gov organizations and businesses. Anonymous and numerous hacker groups linked to the popular collective continue to launch cyber attacks against Russian and Belarussian government organizations and private businesses. In the last few days massive DDoS attacks have taken offline numerous websites of Russian government entities, including the Duma and Ministry of Defense.

IT Governance
FEBRUARY 8, 2022
Welcome to our February 2022 review of phishing attacks, in which we explore the latest scams and the tactics that cyber criminals use to trick people into handing over their personal information. This month, we look at a bogus online contest designed to capture your Facebook login details, the latest Microsoft scam and whether ‘passwordless’ security can mitigate the threat of scams.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Troy Hunt
FEBRUARY 16, 2022
Continuing the march forward to provide governments with better access to their departments' data exposed in breaches , I'm very pleased to welcome the 28th national government onto Have I Been Pwned - New Zealand! They'll join the other govs around the world that have complete free access to breach information impacting their gov domains and TLDs.

eSecurity Planet
FEBRUARY 11, 2022
Risk management is a concept that has been around as long as companies have had assets to protect. The simplest example may be insurance. Life, health, auto, and other insurance are all designed to help a person protect against losses. Risk management also extends to physical devices, such as doors and locks to protect homes and vehicles, vaults to protect money and precious jewels, and police, fire, and CCTV to protect against other physical risks.

Hunton Privacy
FEBRUARY 16, 2022
On February 14, 2022, Texas Attorney General Ken Paxton brought suit against Meta, the parent company of Facebook and Instagram, over the company’s collection and use of biometric data. The suit alleges that Meta collected and used Texans’ facial geometry data in violation of the Texas Capture or Use of Biometric Identifier Act (“CUBI”) and the Texas Deceptive Trade Practices Act (“DTPA”).

Schneier on Security
FEBRUARY 4, 2022
Senators have reintroduced the EARN IT Act, requiring social media companies (among others) to administer a massive surveillance operation on their users: A group of lawmakers led by Sen. Richard Blumenthal (D-CT) and Sen. Lindsey Graham (R-SC) have re-introduced the EARN IT Act , an incredibly unpopular bill from 2020 that was dropped in the face of overwhelming opposition.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.
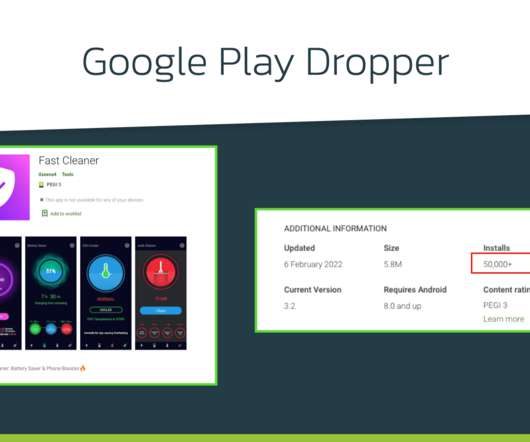
Security Affairs
FEBRUARY 21, 2022
Xenomorph Android trojan has been observed distributed via the official Google Play Store targeting 56 European banks. Researchers from ThreatFabric have spotted a new Android banking trojan, dubbed Xenomorph , distributed via the official Google Play Store that has over 50,000 installations. The banking Trojan was used to target 56 European banks and steal sensitive information from the devices of their customers.

OpenText Information Management
FEBRUARY 22, 2022
The last two years have forced companies and organizations of all sizes to reassess their processes and operational methods and to change their mindset about how best to operate as a business. For OpenText, that has meant doubling down on the product innovations that allow people to reimage how and where they work, how goods … The post Announcing OpenText Cloud Editions 22.1 appeared first on OpenText Blogs.

Troy Hunt
FEBRUARY 5, 2022
I feel like perfect audio remains an unsolved problem for me. Somehow, a low "hiss" has slipped in over the last couple of weeks and messing around trying to solve it before recording this video only served to leave me without any audio at all on the first attempt, and the status quo remaining on the second attempt. And I still can't use my Apollo Twin DAC as an input device almost a year on from when I bought it.

eSecurity Planet
FEBRUARY 23, 2022
How can a hospital protect an MRI machine with an unchangeable password and still connect it to the network? How can an industrial recycler safely secure its $400,000 hard drive recertification rack with control software that only runs on Windows XP? These are not uncommon risks. The devices themselves can’t be secured, but that doesn’t mean we can’t use basic IT techniques to reduce our security risks.

Advertisement
Outdated or absent analytics won’t cut it in today’s data-driven applications – not for your end users, your development team, or your business. That’s what drove the five companies in this e-book to change their approach to analytics. Download this e-book to learn about the unique problems each company faced and how they achieved huge returns beyond expectation by embedding analytics into applications.

Hunton Privacy
FEBRUARY 22, 2022
On February 14, 2022, Noom Inc., a popular weight loss and fitness app, agreed to pay $56 million, and provide an additional $6 million in subscription credits to settle a putative class action in New York federal court. The class is seeking conditional certification and has urged the court to preliminarily approve the settlement. The suit was filed in May 2020 when a group of Noom users alleged that Noom “actively misrepresents and/or fails to accurately disclose the true characteristics of its

Schneier on Security
FEBRUARY 23, 2022
A Berlin-based company has developed an AirTag clone that bypasses Apple’s anti-stalker security systems. Source code for these AirTag clones is available online. So now we have several problems with the system. Apple’s anti-stalker security only works with iPhones. (Apple wrote an Android app that can detect AirTags, but how many people are going to download it?

Security Affairs
FEBRUARY 18, 2022
Iran-linked TunnelVision APT group is actively exploiting the Log4j vulnerability to deploy ransomware on unpatched VMware Horizon servers. Researchers from SentinelOne have observed the potentially destructive Iran-linked APT group TunnelVision is actively exploiting the Log4j vulnerability to deploy ransomware on unpatched VMware Horizon servers. TunnelVision’s TTPs overlap with the ones associated with Iran-linked nation-state actors Phosphorus , Charming Kitten and Nemesis Kitten.
Let's personalize your content