Researcher Finds Malware Targeting Mac Users via Baidu Ad
Data Breach Today
SEPTEMBER 24, 2021
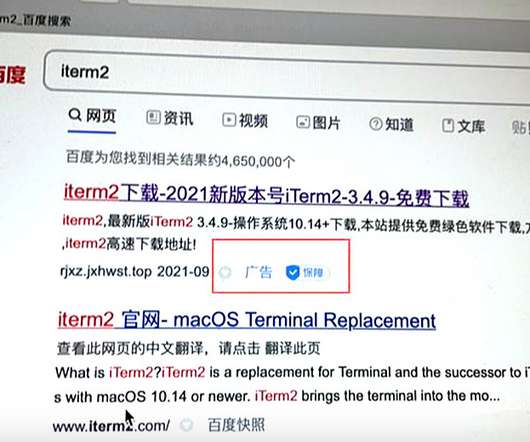
The Ad, Now Deleted, Lured Users to a Phishing Website to Harvest Credentials Chinese security researcher Zhi has discovered a malware targeting Mac users. The malware, spread via a paid advertisement on search engine Baidu, is intended to harvest user credentials, he says. The advertisement has now been taken down.




































Let's personalize your content