Phishing Sites Targeting Scammers and Thieves
Krebs on Security
AUGUST 9, 2021
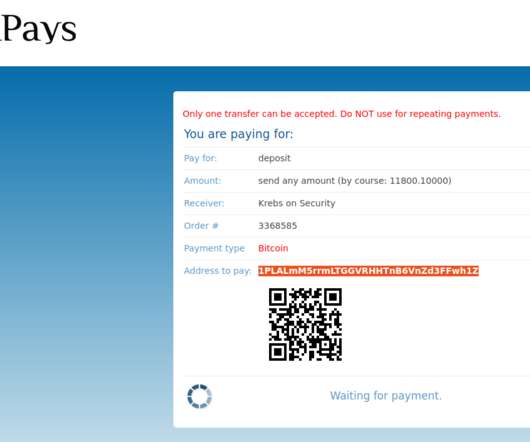
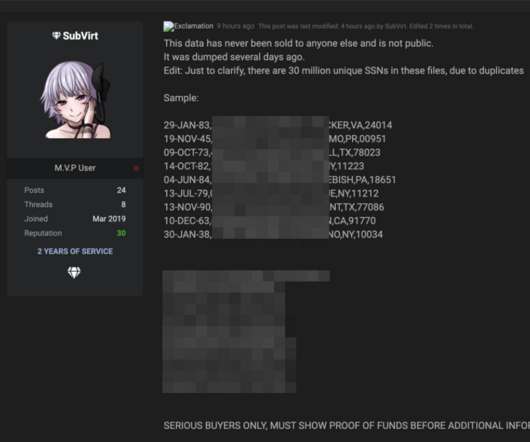
I was preparing to knock off work for the week on a recent Friday evening when a curious and annoying email came in via the contact form on this site: “Hello I go by the username Nuclear27 on your site Briansclub[.]com ,” wrote “ Mitch ,” confusing me with the proprietor of perhaps the underground’s largest bazaar for stolen credit and identity data. “I made a deposit to my wallet on the site but nothing has shown up yet and I would like to know why.” Th

































Let's personalize your content