Homoglyph attacks used in phishing campaign and Magecart attacks
Security Affairs
AUGUST 9, 2020
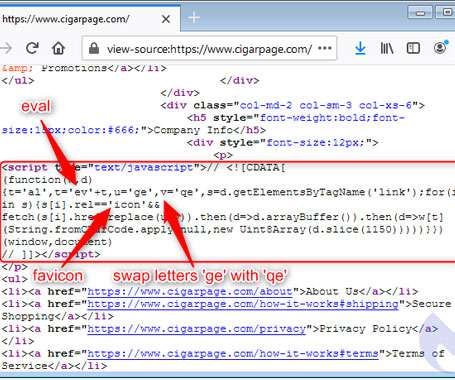
Researchers detailed a new evasive phishing technique that leverages modified favicons to inject e-skimmers and steal payment card data covertly. Researchers from cybersecurity firm Malwarebytes have analyzed a new evasive phishing technique used by attackers in the wild in Magecart attacks. The hackers targeted visitors of several sites using typo-squatted domain names, and modified favicons to inject software skimmers used to steal payment card information.







































Let's personalize your content