Actionable steps you can take today to identify the true risk your organization faces — learn how to separate the exploitable vulnerabilities from the rest.
January 25, 2022

According to a Cisco CISO Benchmark survey, 17% of organizations had 100,000 or more daily security alerts in 2020, and its trajectory has only increased.
2021 followed this trend with a record year of newly discovered CVEs — 20,141 to be exact, topping the 2020 record of 18,325.
More software and an increased digital footprint have led to a record number of vulnerabilities. Aside from this being an indicator of the exposure growth in an organization's attack surface, this unmanageable number makes the defender's job even more difficult, and it also leads to burnout among cybersecurity professionals.
.jpg/?width=700&auto=webp&quality=80&disable=upscale)
Source: Cisco 2020 CISO Benchmark Survey
It's clear that vulnerable does not equal exploitable. In fact, the common ratio between vulnerable in theory and exploitable in practice is 1:100. So how can security teams focus on the true weakness in the vulnerability haystack? The answer lies in the context of a vulnerability, its compensating controls, and the data it leads to.
In this article, we'll provide steps security professionals can take today to identify the true risk their organization faces — how to pinpoint the exploitable vulnerabilities out of the lot.
Below are four steps toward knowing your exploitable attack surface:
Take the Adversarial Perspective
The only way to filter through the sea of vulnerabilities is by attempting to exploit them. That's what an adversary would do. This way, security teams get a concise attack vector pointing to the organization's weakest link. From here, the remediation requests handed to IT are focused, manageable, and based on business impact. And the rest of the vulnerabilities can wait for ongoing patch management tasks. Taking the attacker’s point of view will allow the organization to lead a proactive security program rather than reacting to incidents as they (inevitably) crop up.Cover the Full Scope of Potential Attacks
Adversaries take the path of least resistance to the critical assets. This means using the variety of techniques at their disposal to progress an attack, leveraging any vulnerability and its relevant correlations along the way. Accordingly, the validation methods used must match — they need to go beyond the static vulnerability scan or control attack simulation to include a full penetration test scope. This would cover attack emulation frameworks for security controls, vulnerability and credential strength attacks, network equipment testing, privileged access audits, lateral movement steps, and more.Automate, Automate, Automate
Security validation today must be as dynamic as the attack surface it's securing. Periodical and manual tests are no longer sufficient to challenge the changes an organization undergoes. Security teams need to have an on-demand view of their assets and exposures, and the only way to get there is by automating testing. The growth in digitalization and cloud adoption, remote work, ransomware threats, and recently Log4Shell are just a few examples of how important continuous validation is for security teams to properly defend their organization.Align to MITRE ATT&CK and OWASP Top 10
By aligning to industry standards, security teams ensure that their testing covers the latest adversary techniques. As most attacks succeed by leveraging the most common TTPs, challenging the attack surface against these frameworks provides comprehensive coverage of adversary techniques in the wild. In addition, it allows security executives to clearly report to management on validation of security control efficacy and enterprise readiness against potential threats.
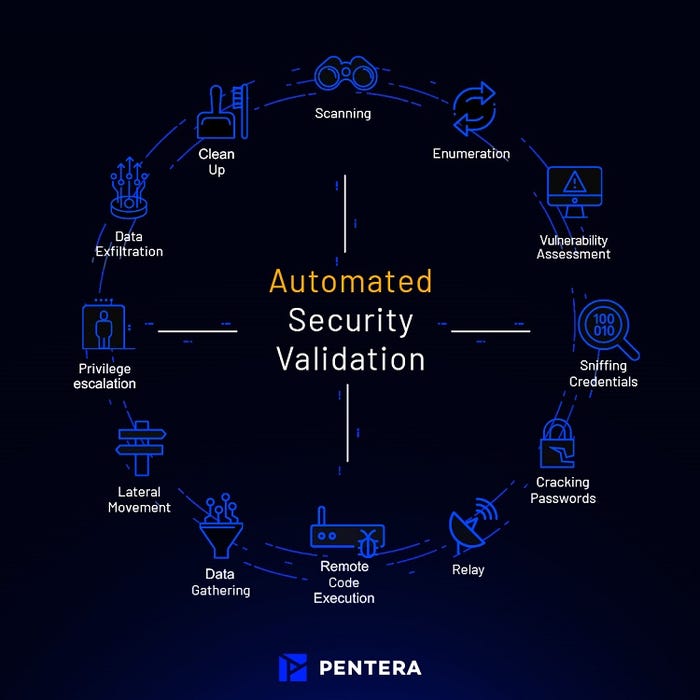
Enter Automated Security Validation
Automated security validation is an advanced approach to testing the integrity of all cybersecurity layers, combining continuous coverage and risk prioritization for effective mitigation of security gaps.
This approach provides a true view of current security exposures by emulating real-life attacks, enabling an impact-based remediation plan rather than chasing thousands of vulnerabilities.
Security teams can know exactly where they stand and confidently strive towards maximum security readiness.
When evaluating security validation platforms make sure to check these boxes:
Agentless, low touch implementation to ensure minimum to no overhead.
Automated, zero playbook, testing, which provides a consistent process for security gap discovery and remediation.
Safely attack the production network, leveraging ethical exploits to emulate the adversary without disrupting business operations.
Validate the entire security stack with full scope of real-world techniques aligned to industry frameworks.
Expose security gaps in cloud workloads and emulate lateral expansion weaknesses from on-premises to the cloud to the remote workforce.
Immediate reporting that provides a prioritized list of which vulnerabilities are critical to fix based on business impact.
The question that needs answering is whether you know your organization's true security risk at any given time. Do you know where the organization's weakest links are so they can be remediated or mitigated before an attacker leverages them toward an attack?
If you're ready to validate your organization against the latest threats including ransomware strains and Log4Shell vulnerabilities, request a free security health check.
About the Author

Omer Zucker is the Product Team Lead at Pentera, with over 15 years of information security experience. Before joining Pentera, Omer established and led the Security Intelligence Center at Mercedes-Benz R&D in Tel Aviv. Omer served as an IDF officer in the elite cybersecurity unit 8200, in various defensive cybersecurity positions.
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


