Volkswagen, Audi Notify 3.3 Million of Data Breach
Data Breach Today
JUNE 15, 2021
Data Was Left Unsecured by Unidentified Marketing Services Company Volkswagen and its Audi subsidiary are notifying 3.3 million people in the U.S and Canada of a breach of personal information by a marketing services supplier. Volkswagen says 90,000 of those affected may have also had their driver's license number, loan data and other personal information exposed.











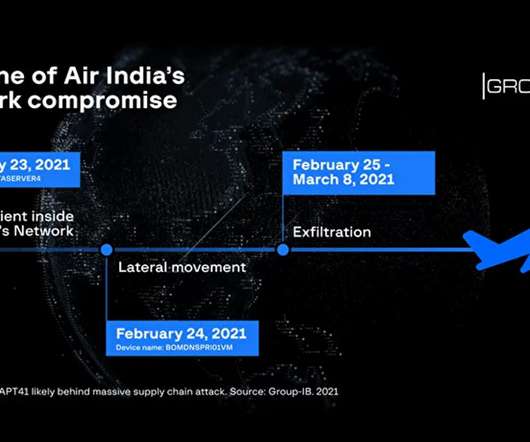
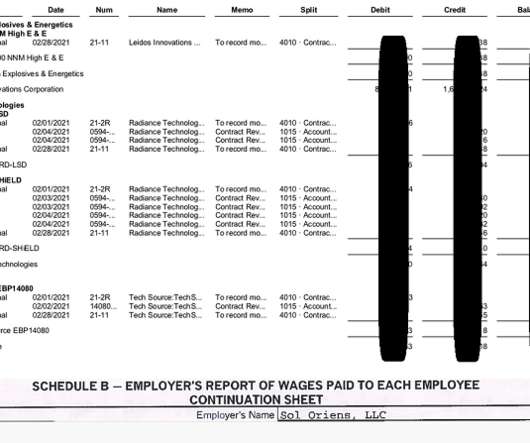












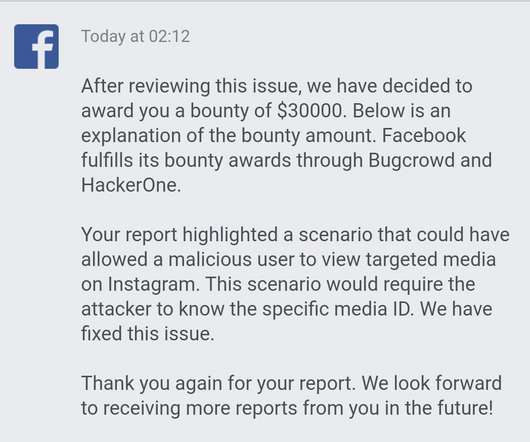












Let's personalize your content