Source code of Dharma ransomware now surfacing on public hacking forums
Security Affairs
MARCH 29, 2020
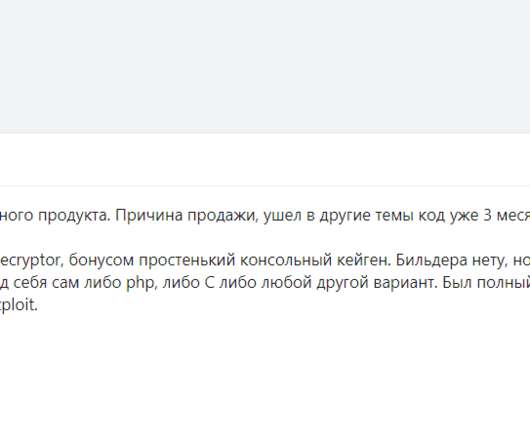
The source code of the infamous Dharma ransomware is now available for sale on two Russian-language hacking forums. The source code of one of the most profitable ransomware families, the Dharma ransomware , is up for sale on two Russian-language hacking forums. The Dharma ransomware first appeared on the threat landscape in February 2016, at the time experts dubbed it Crysis.












Let's personalize your content