All the Ways Facebook Tracks You—and How to Limit It
WIRED Threat Level
JANUARY 12, 2020
If you have a Facebook account—and even if you don't—the company is going to collect data about you. But you can at least control how it gets used.

WIRED Threat Level
JANUARY 12, 2020
If you have a Facebook account—and even if you don't—the company is going to collect data about you. But you can at least control how it gets used.

Security Affairs
JANUARY 12, 2020
Last week, Senator Tom Cotton (R-Arkansas) introduced a bill that would ban intelligence sharing with countries that use Huawei 5G networks. Senator Tom Cotton (R-Arkansas) has introduced this week a new bill that would ban the sharing of intelligence with countries that use Huawei equipment on their fifth-generation (5G) networks. Since November 2018, the US Government has invited its allies to exclude Chinese equipment from critical infrastructure and 5G architectures over security concerns.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Adam Shostack
JANUARY 12, 2020
Andrew McCarthy has an amazing and impressive photographs of the moon on Instagram. To call these photographs is somewhat provocative. In his trilogy, Ansel Adams focuses (sorry! Not sorry) on composition, exposure, and development. By exposure, he specifically meant exposing film to light in controlled ways that caused chemical reactions on the film, and it remains common to hear photographers talk of ‘an exposure’, in much the same way that we dial phones.
Security Affairs
JANUARY 12, 2020
Google revealed it successfully removed more than 1,700 apps from the Play Store over the past three years that had been infected with the Joker malware. Google provided technical details of its activity against the Joker malware (aka Bread) operation during the last few years. The Joker malware is a malicious code camouflaged as a system app and allows attackers to perform a broad range of malicious operations, including disable the Google Play Protect service , install malicious apps, generate

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

eDiscovery Daily
JANUARY 12, 2020
A two-topic day for us with a couple of terrific educational opportunities! One free CLE educational program in Houston comes up in just ten days! And, the other happens in Florida and currently has early bird pricing available for a wonderful full day conference in March! ACEDS Houston Event. Our first event of the year in the Houston chapter of the Association of Certified E-Discovery Specialists (ACEDS) is on Thursday, January 23rd from noon to 1:30pm CT at The Houston Club at 910 Louisiana
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Archives Blogs
JANUARY 12, 2020
Protege todos tus documentos importantes: Cómo encriptar tus archivos y carpetas [link]. Solemos trabajar con información importante, privada y confidencial que no queremos que llegue a manos de cualquier persona y que pueda usarla en nuestra contra. Información personal, información confidencial de trabajo, estudios, investigaciones… Hay documentos que no queremos compartir o poner en peligro.
Security Affairs
JANUARY 12, 2020
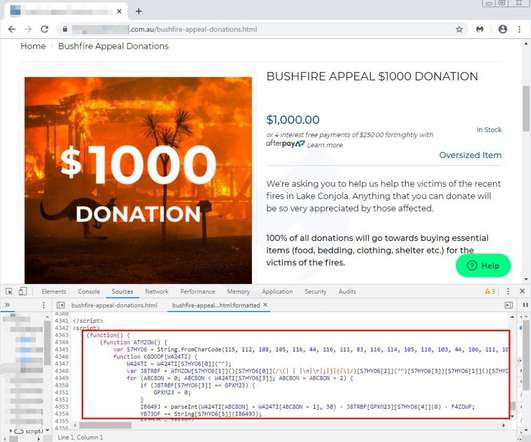
A new MageCart attack made the headlines, crooks installed a software skimmer on a website that collects donations for the victims of the Australia bushfires. Experts from Malwarebytes have discovered a new Magecart attack that compromised a website collecting donations for the victims of the Australia bushfires. #Magecart skimmer stealing from folks donating to Australia's bushfire effort.

Archives Blogs
JANUARY 12, 2020
CÓMO ENVIAR ARCHIVOS DE FORMA RÁPIDA ENTRE MÓVILES CON WIFI DIRECT [link]. Según evoluciona la tecnología se van creandonuevos y mejorados métodos de transmisión, si echamos la vista atrás recordaremos los infrarrojos o uno más actual como es la tecnología Bluetooth, la cual era muy común utilizarla para enviar archivos, pero tardaba demasiado. En la actualidad existe un método que ha surgido como solución a nuestros problemas de transferencia de archivos, se llama WiFi Direct y cada vez está má

Archives Blogs
JANUARY 12, 2020
Compartir archivos: 3 razones lo hacen un imprescindible. [link]. El conocido “negocio tradicional” ha desaparecido. La tecnología y los dispositivos han cambiado nuestra forma de trabajar, ya sea en una fábrica o en cualquier oficina reconocida. Con la evolución y desarrollo de dispositivos enfocados a las áreas muchas cosas se han transformado para siempre, pero lo que no ha cambiado es la necesidad de colaboración.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Archives Blogs
JANUARY 12, 2020
El final del papel en las oficinas [link]. El trabajo de la empresa compostelana Unayta se basa en ayudar a las compañías e instituciones a dar el salto definitivo hacia la digitalización de su día a día. Terminan con los documentos, pero también se dedican a la transformación, conservación y difusión de archivos históricos. Ellos acompañan a las empresas y administraciones públicas en uno de los retos más importantes que han tenido que afrontar en las últimas décadas.

Archives Blogs
JANUARY 12, 2020
No pierdas tus archivos con los mejores programas de recuperación de datos [link]. Hay muchas causas por las que podemos perder nuestros archivos personales. Por ejemplo, un fallo en el disco duro, un virus, un error en Windows, incluso por errores humanos. Siempre recomendamos contar con copias de seguridad de nuestros datos más importantes de manera que. si ocurre algo, podemos recuperarlos rápidamente y no perdamos ese material que, aunque pueda no tener valor económico, tiene un gran valor s
Let's personalize your content