3-Year JS Injection Campaign Targets 51,000 Websites
Data Breach Today
MARCH 25, 2023
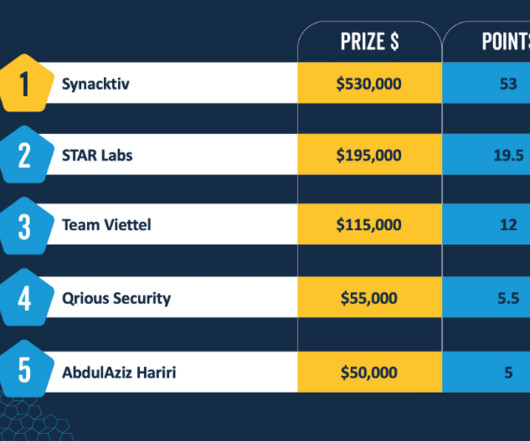
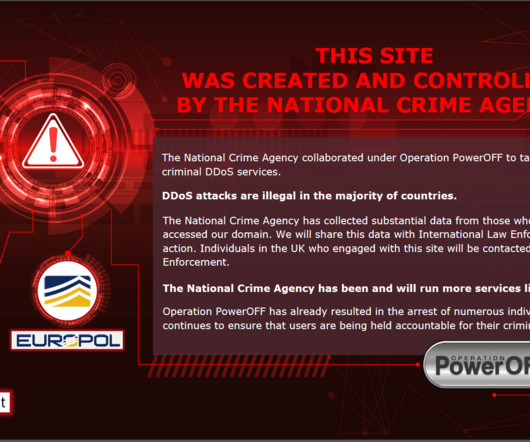
Campaign Peaked in 2022, Continues to Infect Websites Using Obfuscation Tactics A widespread ongoing malicious JavaScript injection campaign first detected in 2020 has targeted over 51,000 websites, redirecting victims to malicious content like adware and scam pages. Attackers are using several obfuscation tactics to bypass detection.













Let's personalize your content