Hackers Impersonate Amnesty International to Spread Malware
Data Breach Today
OCTOBER 2, 2021
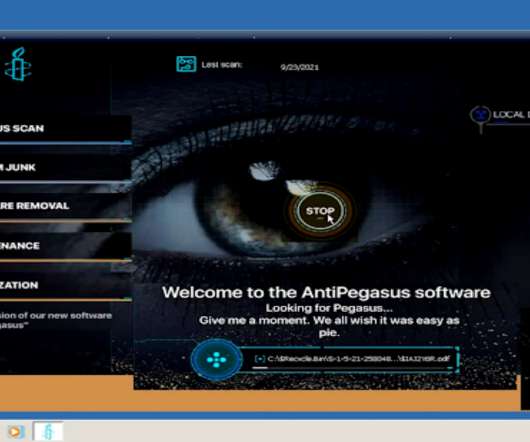
Sarwent Malware Can Execute Remote Tasks Fraudsters are impersonating Amnesty International by building a fake site to distribute malware purporting to be an anti-virus tool to protect against the NSO Group's Pegasus tool, according to researchers at Cisco Talos.













Let's personalize your content