UK Companies Fear Reporting Cyber Incidents, Parliament Told
Data Breach Today
NOVEMBER 29, 2022
Firms Fear that Involving Police in Response Will Have Regulatory Consequences U.K. businesses shy from involving police in cyber incident response for fear of regulatory consequences, lawmakers sitting on Parliament's Joint Committee on National Security Strategy heard. Allowing businesses to anonymously disclose incidents would result in more data, suggested a witness.



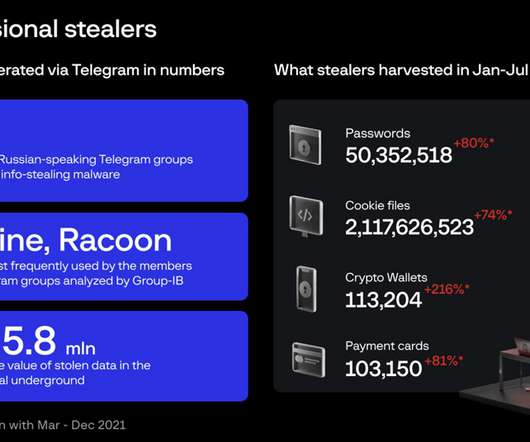



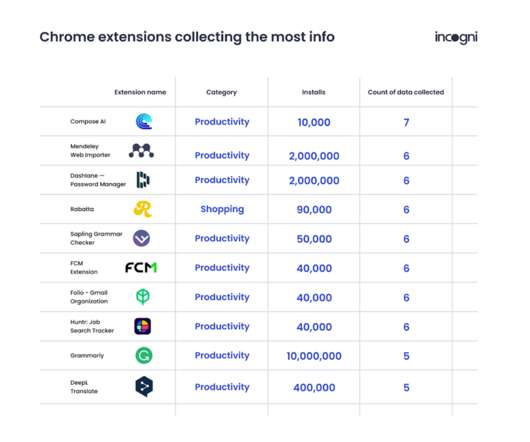


































Let's personalize your content