APT Group Kimsuky Has New Attack Technique, Researchers Say
Data Breach Today
JUNE 9, 2021
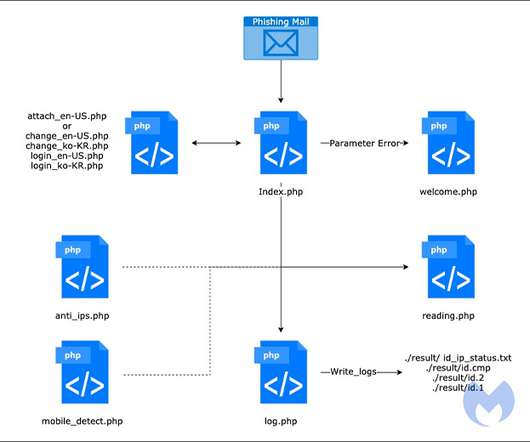
South Korean Government Reportedly Targeted Using AppleSeed Backdoor Researchers at Malwarebytes have uncovered the latest tactics, techniques, and procedures used by the North Korean threat group Kimsuky, also known as Thallium, Black Banshee and Velvet Chollima, as it continues to launch espionage attacks. This time it is using an AppleSeed backdoor.







































Let's personalize your content