Cyber Incident Knocks Construction Firm Palfinger Offline
Data Breach Today
JANUARY 25, 2021
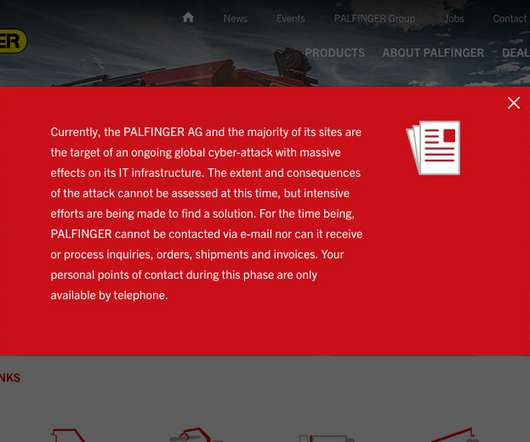
Unknown Attack Has Disrupted the Company's Global IT Infrastructure The Austrian construction equipment manufacturing firm Palfinger AG reports being hit with a cyberattack that has knocked the majority of its worldwide IT infrastructure offline, eliminating its ability to use email and conduct business.





































Let's personalize your content