Fraudsters Alter Election Phishing Scam
Data Breach Today
OCTOBER 26, 2020
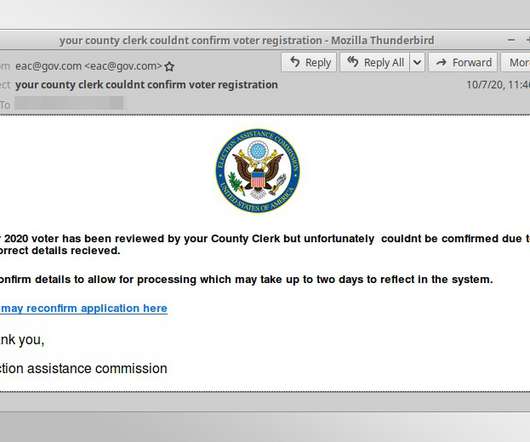
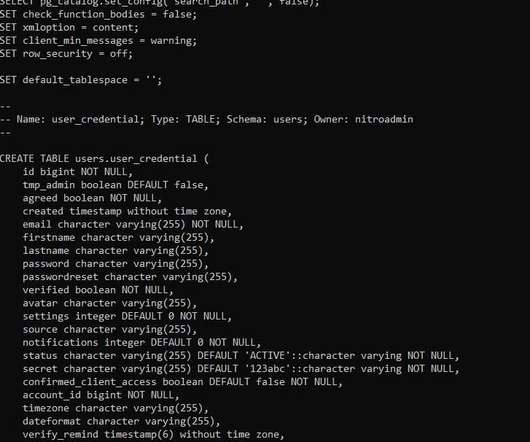
Scammers Now Attempting to Steal Banking and Driver's License Information Fraudsters operating an election-themed phishing campaign have tweaked their malicious landing pages to harvest more information, including banking credentials, account data and vehicle identification information, Proofpoint reports.






































Let's personalize your content