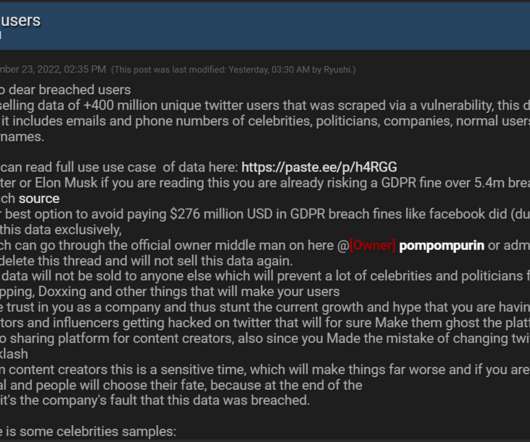
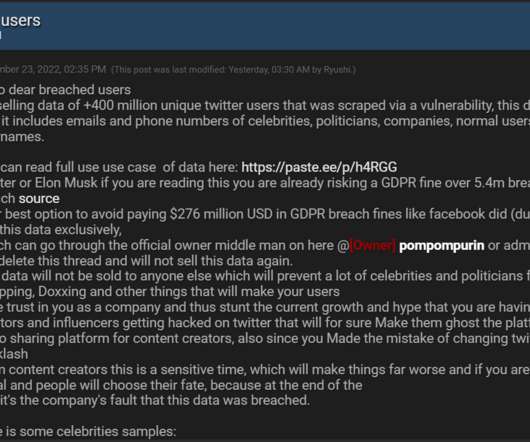
Hacker Claims to Have Scraped 400M Twitter User Records
Data Breach Today
DECEMBER 25, 2022
Regulatory Pressure over Security, Privacy Mounts on Beleaguered Social Media Firm A member of a criminal data breach forum says he's selling email addresses and phone numbers of 400 million Twitter users. If verified, the data breach would be a further blow to Twitter and its beleaguered chief executive as regulators increase pressure over the firm's security practices.





















Let's personalize your content