Russia Says It's Seen 'Unprecedented' Level of Cyberattacks
Data Breach Today
MARCH 18, 2022
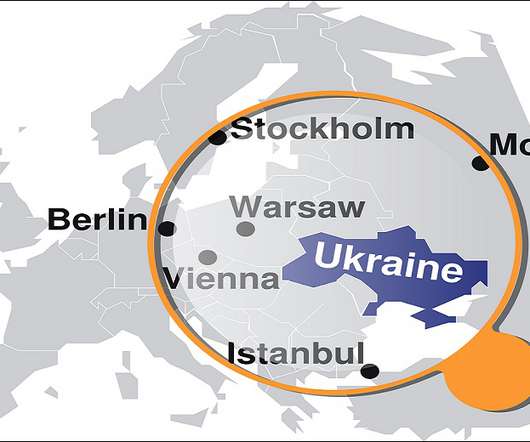
Also: Anonymous Continues Its Cyberwar Against the Russian Government As the Ukrainian military resists Russian advances toward its major population centers, its IT security teams are contending with record cyber incidents - although the same is true of their eastern neighbors, with Russia reporting "unprecedented" cyberattacks on its networks.







































Let's personalize your content