Webinar Recap: Three Things You Need to Know About Slack’s New Legal Hold
Hanzo Learning Center
NOVEMBER 10, 2021
If your organization uses Slack for business communications, how are you preserving Slack data for potential litigation?

Hanzo Learning Center
NOVEMBER 10, 2021
If your organization uses Slack for business communications, how are you preserving Slack data for potential litigation?
Krebs on Security
NOVEMBER 10, 2021
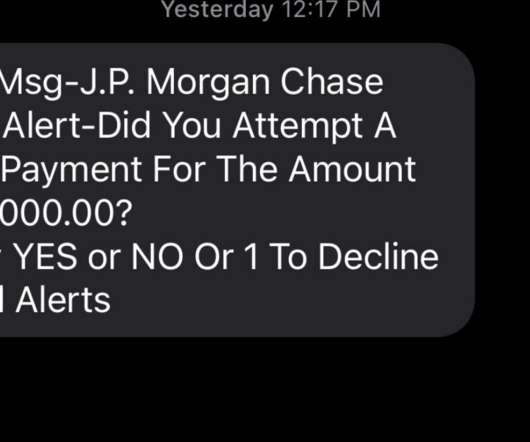
Most of us have probably heard the term “smishing” — which is a portmanteau for traditional ph ishing scams sent through SMS text messages. Smishing messages usually include a link to a site that spoofs a popular bank and tries to siphon personal information. But increasingly, phishers are turning to a hybrid form of smishing — blasting out linkless text messages about suspicious bank transfers as a pretext for immediately calling and scamming anyone who responds via text
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
NOVEMBER 10, 2021
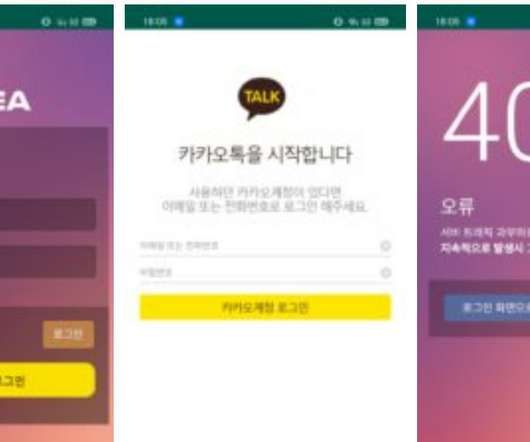
South Korean users have been targeted with a new sophisticated Android spyware, tracked as PhoneSpy, as part of an ongoing campaign. Researchers from Zimperium zLabs uncovered an ongoing campaign aimed at infecting the mobile phones of South Korean users with new sophisticated android spyware dubbed PhoneSpy. The malware already hit more than a thousand South Korean victims.

Threatpost
NOVEMBER 10, 2021
The distributed computing vendor patched the flaw, affecting Citrix ADC and Gateway, along with another flaw impacting availability for SD-WAN appliances.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Security Affairs
NOVEMBER 10, 2021
Researchers have identified a total of 14 new vulnerabilities in BusyBox that expose million of Unix-based devices to cyberattacks. Researchers from software development company JFrog and industrial cybersecurity firm Claroty have identified a total of 14 new critical vulnerabilities in BusyBox. The software is used by many network appliances and embedded devices with limited memory and storage resources.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Dark Reading
NOVEMBER 10, 2021
AWS fixed the security flaws that left the API service at risk of so-called HTTP header-smuggling attacks, says the researcher who discovered them.

Threatpost
NOVEMBER 10, 2021
Researchers have a working exploit for the vulnerability (now patched), which allows for unauthenticated RCE and affects an estimated 70,000+ VPN/firewalls.

Schneier on Security
NOVEMBER 10, 2021
I just don’t think it’s possible to create a hack-proof computer system, especially when the system is physically in the hands of the hackers. The Sony Playstation 5 is the latest example: Hackers may have just made some big strides towards possibly jailbreaking the PlayStation 5 over the weekend, with the hacking group Fail0verflow claiming to have managed to obtain PS5 root keys allowing them to decrypt the console’s firmware. […].

Dark Reading
NOVEMBER 10, 2021
OT security engineers and personnel should approach senior management with an emphasis on risk reduction benefits and with a concrete plan to secure budget and funding before it's too late.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

IT Governance
NOVEMBER 10, 2021
ISO 45001 is the international standard for occupational health and safety. Its purpose is to reduce injuries and diseases in the workplace, including the promotion and protection of physical and mental health. This is an issue that’s more important than ever, with 1.9 million deaths and 360 million injuries each year from workplace incidents. In this blog, we look at each clause of ISO 45001 to understand how it works and what you must do to achieve compliance.

Hunton Privacy
NOVEMBER 10, 2021
On November 10, 2021, the UK Supreme Court issued its long-awaited judgment in the Lloyd v Google case. The decision is expected to make it difficult in practice for a future class action lawsuit that is brought on behalf of a class of individuals who have not actively opted in to being represented by the lead claimant to proceed under UK law. The Lloyd case concerned alleged violations by Google in 2011 and 2012 of the UK Data Protection Act 1998 (the “DPA”) in connection with the collection an

Security Affairs
NOVEMBER 10, 2021
Citrix addressed two vulnerabilities affecting Citrix ADC, Gateway, and SD-WAN, one of them is a critical issue leading to DoS. Citrix has released security updates to address two vulnerabilities in ADC, Gateway, and SD-WAN, including a critical flaw, tracked as CVE-2021-22955, that can be exploited to trigger a denial of service (DoS) condition. The CVE-2021-22955 DoS vulnerability affects Citrix Application Delivery Controller (ADC) and Gateway devices that have been configured as a VPN (Gatew

Dark Reading
NOVEMBER 10, 2021
Russian-speaking "Void Balaur" group's victims include politicians, dissidents, human rights activists, doctors, and journalists, security vendor discloses at Black Hat Europe 2021.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Data Protection Report
NOVEMBER 10, 2021
On 10 November 2021, the UK Supreme Court handed down the much anticipated judgment in Lloyd v Google LLC [2021] UKSC 50, unanimously allowing Google’s appeal and reversing the decision of the Court of Appeal. In summary, the Supreme Court ruled that damages for “loss of control” are not available for breach of the Data Protection Act 1998 ( DPA 1998 ), and that even if loss of control damages had been available, the claim could not be brought as a representative action as it would still have be

DLA Piper Privacy Matters
NOVEMBER 10, 2021
On 10 November 2021, the UK Supreme Court, in a unanimous judgment, allowed Google’s appeal against the Court of Appeal decision granting Mr Lloyd permission to continue his representative claim (i.e. a US-style opt-out “class action”) against Google. The judgment brings very welcome clarification in a rapidly evolving area of English law relating to representative “class” actions in general, and in the context of data protection regimes specifically.

IG Guru
NOVEMBER 10, 2021
Are there gaps in your information governance program? Is your organization leading or falling behind others in your industry? Now in its third year, the IG Maturity Index Survey continues to create the industry-standard benchmark for information governance. The first 200 participants to complete the survey will receive a $5 gift card, and all participants […].

Security Affairs
NOVEMBER 10, 2021
A critical vulnerability in the WP Reset PRO WordPress plugin can allow an authenticated user to wipe the entire database of WordPress sites. Researchers from cybersecurity form Packstack have discovered a critical vulnerability in the WP Reset PRO WordPress plugin that could be exploited by an authenticated user to completely wipe the database of a website.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Threatpost
NOVEMBER 10, 2021
PhoneSpy already has stolen data and tracked the activity of targets in South Korea, disguising itself as legitimate lifestyle apps.

Security Affairs
NOVEMBER 10, 2021
Taiwan ‘s government agencies face around five million cyberattacks and probes every day, most of them from China. Around five million cyber attacks hit Taiwan’s government agencies every day, and most of the hacking attempts are originated from China. Cyber security department director Chien Hung-wei told parliament representatives that government infrastructure faces “five million attacks and scans a day” . “We are strengthening the government’s defensive m

Dark Reading
NOVEMBER 10, 2021
Companies are relying more heavily on third parties, remote employees, and partners, expanding their attack surface area beyond traditional boundaries.

OpenText Information Management
NOVEMBER 10, 2021
OpenText World 2021 kicks off in less than a week and the OpenText Content Cloud™ team is excited for this opportunity to connect with so many of our Content Services customers—and new customers as well. There’s a great line-up of informative sessions within the Content Cloud track at OpenText World, and while we hope you … The post Join us at an OpenText World Meet up appeared first on OpenText Blogs.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
NOVEMBER 10, 2021
Wiz researchers who discovered a severe flaw in the Azure Cosmos DB database discussed the full extent of the vulnerability at Black Hat Europe.

Jamf
NOVEMBER 10, 2021
Together, Carousel Cloud and Jamf MDM enhance the native capabilities of Apple TV, making it the perfect digital media player for conveying information and inspiration to your workers.

Dark Reading
NOVEMBER 10, 2021
The exercise included several objectives related to response procedures at the refinery, including evacuation and shelter-in-place decision-making; roles and responsibilities during investigations; communication with first responders; and public messaging before and following an incident.

Collibra
NOVEMBER 10, 2021
Large enterprises around the world use Tableau to solve some of the hardest business problems. Tableau’s analytics platform helps organizations understand their data so that they can make smart business decisions. But how do Tableau users confidently build dashboards and workbooks without data context and data quality metrics? Collibra helps solve this problem by providing an integrated data governance and data catalog solution that helps Tableau users find the best data, understand its context

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Dark Reading
NOVEMBER 10, 2021
The Dependency Combobulator is an open source Python-based toolkit that helps developers discover malicious software components that may have accidentally been added to their projects.

Jamf
NOVEMBER 10, 2021
Discover an educational solution that streamlines workflows for teachers, students, parents and administrators. Educators in Georgia used an innovative distributed learning model along with Jamf School to rapidly deploy an iPad fleet and help students to feel a sense of ownership of their devices.

Dark Reading
NOVEMBER 10, 2021
One size won't fit all as we try to reconcile the need to demonstrate expertise and value with keeping clients and researchers safe.
Let's personalize your content