Good News: REvil Ransomware Victims Get Free Decryptor
Data Breach Today
SEPTEMBER 17, 2021
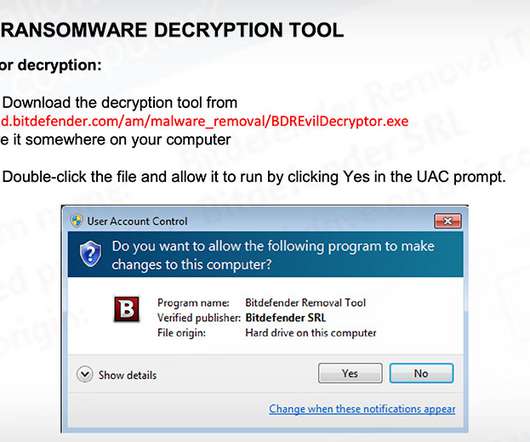
Many Files Crypto-Locked Before July 13 Unlockable via Free Bitdefender Decryptor Score one for the good guys in the fight against ransomware: Anyone who fell victim to REvil, aka Sodinokibi, crypto-locking malware before July 13 can now decrypt their files for free, thanks to a decryptor released by security firm Bitdefender.






































Let's personalize your content