T-Mobile USA Investigates Possible Data Breach
Data Breach Today
AUGUST 16, 2021
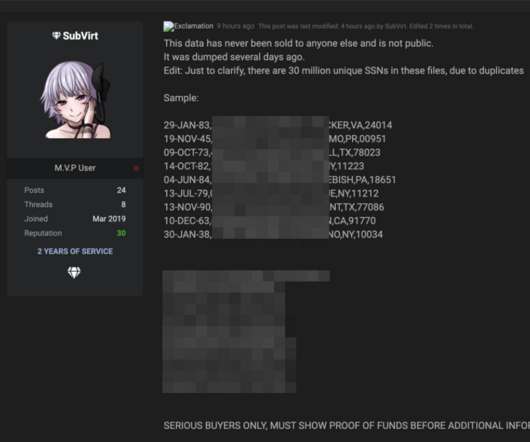
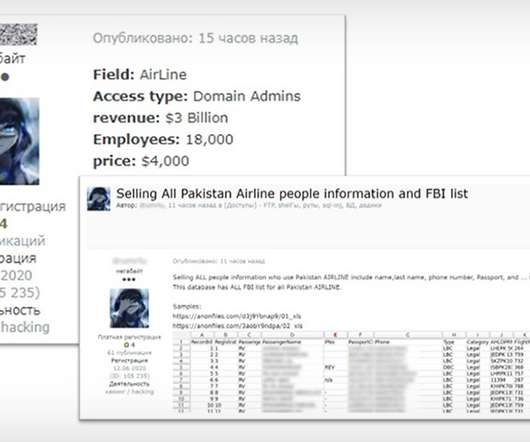
Group Claims GGSN Misconfiguration Led to 100 Million User Accounts T-Mobile USA says it is investigating a claim that as many as 100 million accounts may have been compromised in a data breach. The person who claims responsibility for the alleged breach says T-Mobile misconfigured a Gateway GPRS Support Node.






























Let's personalize your content