Analysis: 2020 Health Data Breach Trends
Data Breach Today
JANUARY 4, 2021
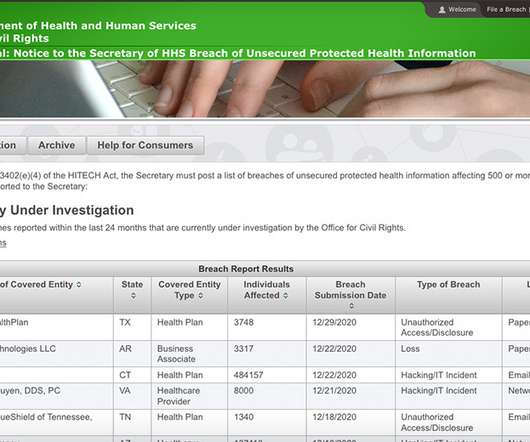
Ransomware, Phishing Incidents, Vendor Hacks Prevail Hacking incidents, including ransomware and phishing attacks, as well as security incidents involving vendors dominated the federal tally of major health data breaches in 2020.









































Let's personalize your content