Suspected InfinityBlack Hackers Arrested
Data Breach Today
MAY 6, 2020
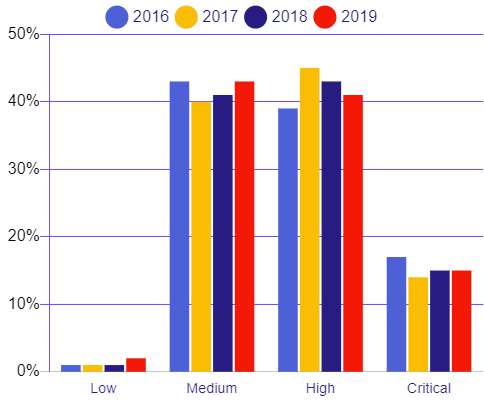
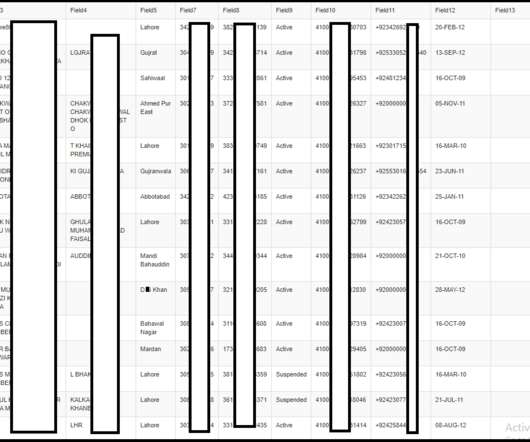
Cybercriminals Had Access to Millions of User Credentials, Police Say Five suspected members of the InfinityBlack hacking group have been arrested, and authorities in Europe say they've seized two databases with more than 170 million entries, including combinations of stolen usernames and passwords.






































Let's personalize your content