Coronavirus Cybercrime Victims: Please Come Forward
Data Breach Today
MARCH 20, 2020
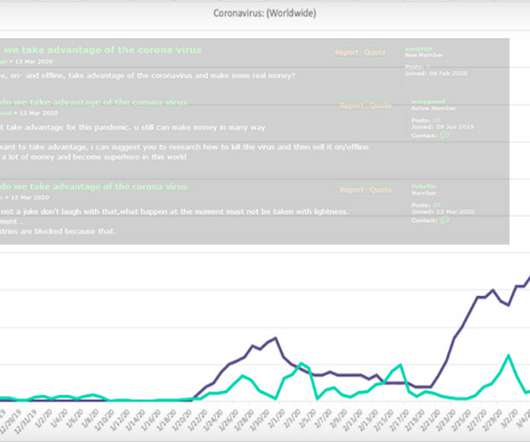
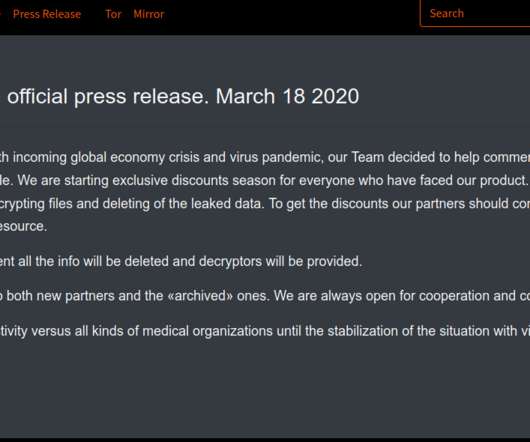
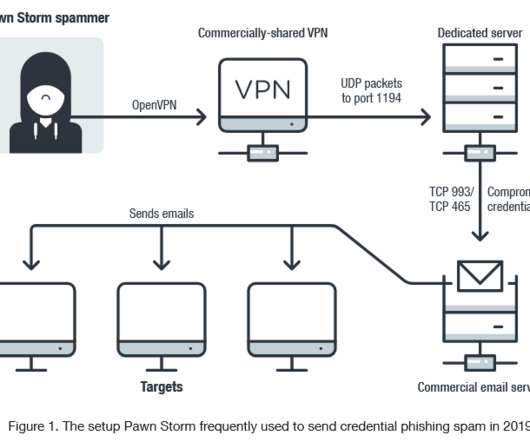
Businesses Asked to Report COVID-19-Themed Crime to Police As cybercriminals and nation-states take advantage of the COVID-19 pandemic to further their own aims, authorities are calling on victims to report online attacks as quickly as possible to help them better disrupt such activity.





































Let's personalize your content