Spanish Banking Trojan Attacks Various Industry Verticals
Data Breach Today
AUGUST 20, 2022
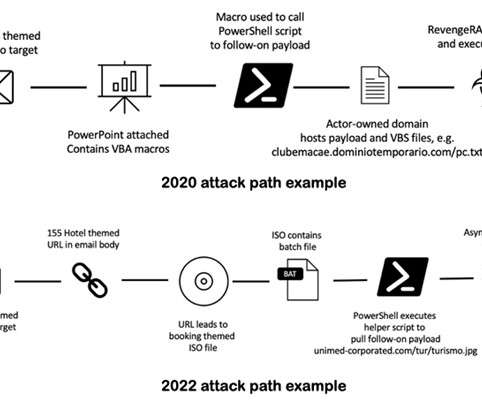
Grandoreiro Banking Trojan Impersonates Mexican Government Officials Researchers uncovered a spear-phishing campaign targeting automotive and chemical manufacturers across the Spanish-speaking nations of Mexico and Spain. The latest campaign began in June 2022, uses Grandoreiro banking Trojan and impersonates Mexican government officials, Zscaler ThreatLabz reports.













Let's personalize your content