Feds Warn Healthcare Entities of 'Evernote' Phishing Scheme
Data Breach Today
AUGUST 12, 2022
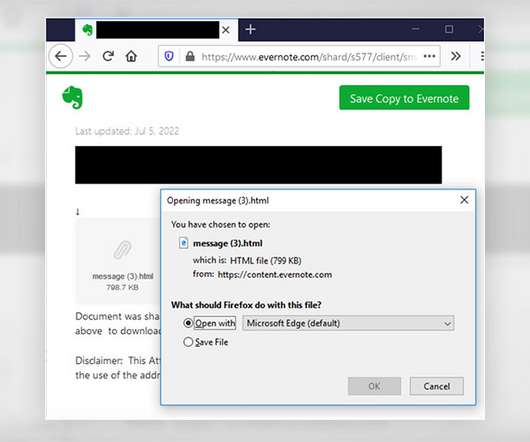
Scam Uses 'Secure Message' Theme and Trojan to Harvest Credentials A "secure message-themed" phishing campaign targeting healthcare providers aims to lure recipients to an Evernote notepad website in an attempt by hackers to harvest security credentials, federal authorities warn, saying the scheme puts entities at risk for potential data security compromises.








































Let's personalize your content