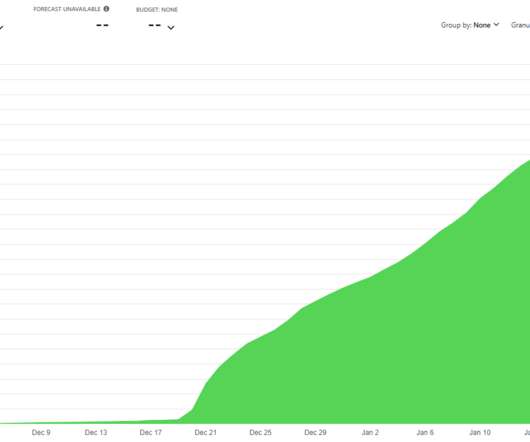
How I Got Pwned by My Cloud Costs
Troy Hunt
JANUARY 23, 2022
I have been, and still remain, a massive proponent of "the cloud" I built Have I Been Pwned (HIBP) as a cloud-first service that took advantage of modern cloud paradigms such as Azure Table Storage to massively drive down costs at crazy levels of performance I never could have achieved before. I wrote many blog posts about doing big things for small dollars and did talks all over the world about the great success I'd had with these approaches.















Let's personalize your content