Startup Probes Hack of Internet-Connected Security Cameras
Data Breach Today
MARCH 10, 2021
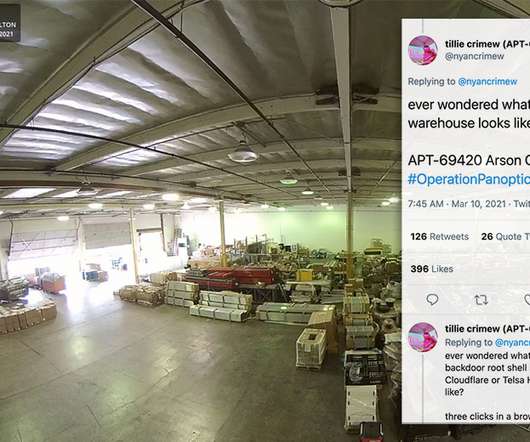
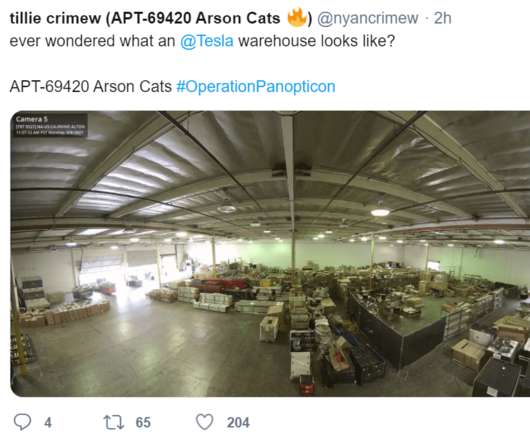
'Arson Cats' Researchers Say Device Flaws Gave Them Full Access to Verkada Cameras The "Arson Cats" research group says it was able to exploit flaws in internet-accessible security cameras built by Silicon Valley "cloud-based enterprise video security" startup Verkada to access live video and audio feeds from inside Tesla, Okta and Cloudflare offices, plus healthcare facilities and prisons.







































Let's personalize your content