New Malicious Adware Exploits Apple M1 Chip
Data Breach Today
FEBRUARY 20, 2021
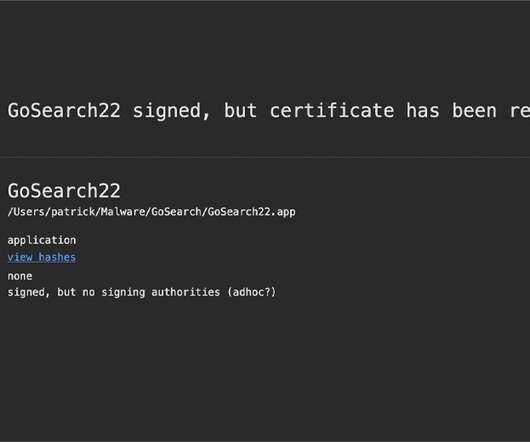
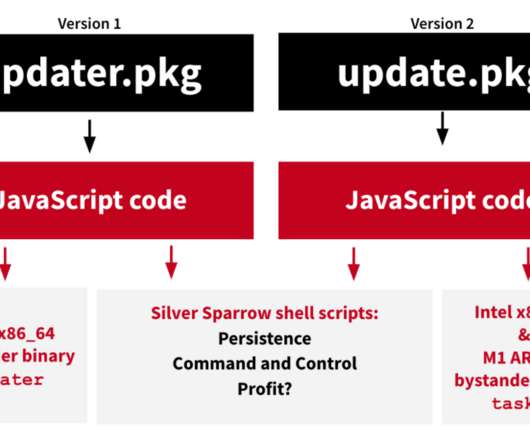
GoSearch22 is an Off-Shoot of macOS-Targeting Pirrit Adware A security researcher has uncovered what is believed to be the first-ever malware variant that can be successfully executed in Apple's M1 chips, its latest central processor unit for Mac computers.














Let's personalize your content