Ransomware: Call Centers Cold-Call Victims to Demand Ransom
Data Breach Today
DECEMBER 7, 2020
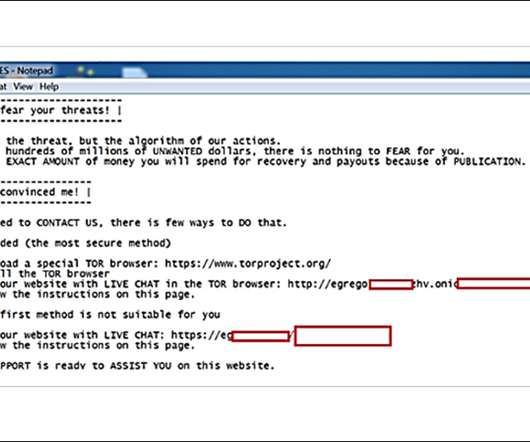
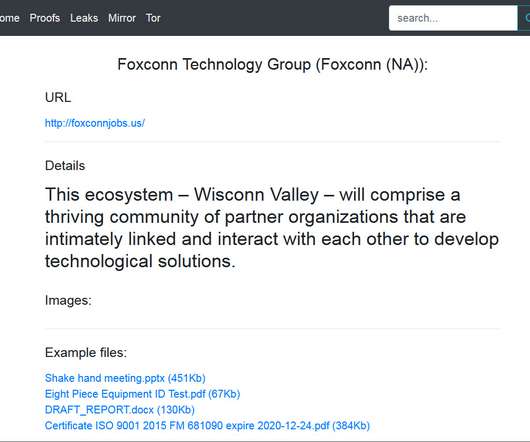
Such Specialization Highlights Ransomware Operators' Increasing Business Savvy Ransomware innovation seems to know no bounds, as crime gangs seek new ways to make crypto-locking malware ever more profitable. Beyond data-leak sites and affiliate programs, gangs have also been using call centers to cold-call victims, tell them they've been hit by ransomware, and request payment.







































Let's personalize your content