A data breach broker is selling account databases of 17 companies
Security Affairs
NOVEMBER 1, 2020
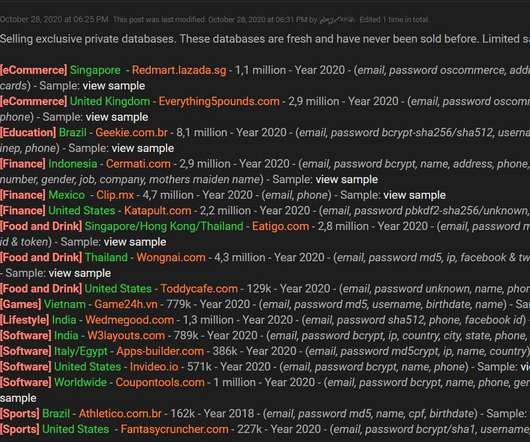
A threat actor is offering for sale account databases containing an aggregate total of 34 million user records stolen from 17 companies. A data breach broker is selling account databases containing a total of 34 million user records stolen from 17 companies. The threat actor is advertising the stolen data since October 28 on a hacker forum. Source Bleeping Computer.
















Let's personalize your content