Nephilim Ransomware Gang Tied to Citrix Gateway Hacks
Data Breach Today
JUNE 22, 2020
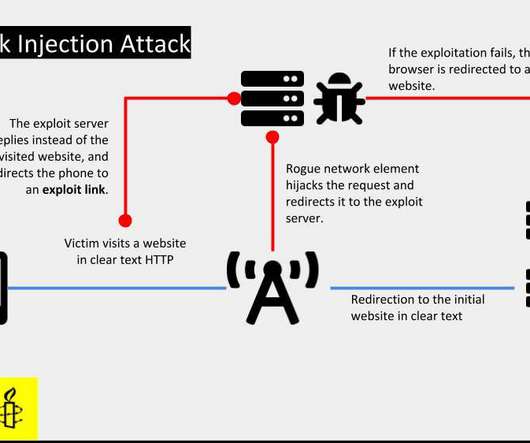
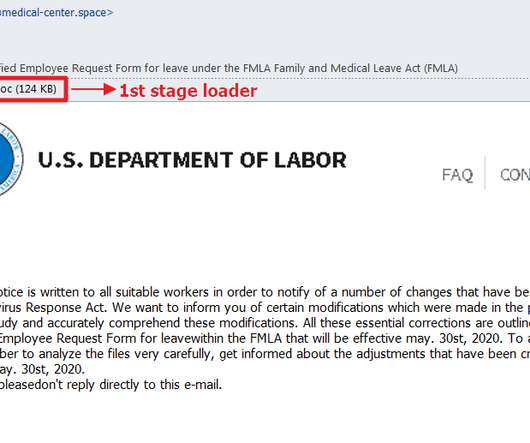
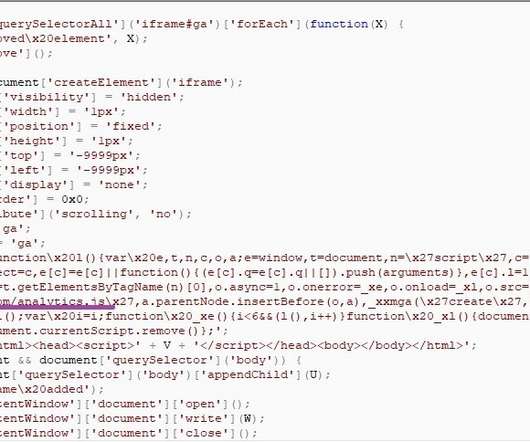
Campaign Targets Unpatched Software and Weak Authentication, Defenders Warn Hackers wielding Nefilim ransomware are targeting unpatched or poorly secured Citrix remote-access technology, then stealing data, unleashing crypto-locking malware and threatening to dump data to try to force payment, New Zealand's national computer emergency response team warns.






































Let's personalize your content