Data compliance challenges in an as-a-service world
Information Management Resources
DECEMBER 17, 2019
Organizations are increasingly coming to rely on software-as-a-service, replacing applications that have previously been hosted on-premises.
Information Management Resources
DECEMBER 17, 2019
Organizations are increasingly coming to rely on software-as-a-service, replacing applications that have previously been hosted on-premises.

Dark Reading
DECEMBER 17, 2019
How to move beyond one-off campaigns and build a true security awareness program.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Record Nations
DECEMBER 17, 2019
There are two main ways of managing files digitally—DMS systems and cloud storage—and while each provide the same basic advantages of going digital, they also have differences that can make one better than the other depending on factors like how much data you need to manage and what your budget looks like. Learn more in […]. The post Creating a Records Management Plan: Is a DMS or Cloud Storage Better?

Data Breach Today
DECEMBER 17, 2019
Anthony Cardoza of XTN Cognitive Security on Defensive Measures Fraud prevention is a perpetual cat-and-mouse game as fraudsters develop new tools and uncover new ways to monetize their activities, says Anthony Cardoza of XTN Cognitive Security, who offers defensive insights.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

AIIM
DECEMBER 17, 2019
With the new year just a few weeks away, many have shifted their day-to-day focus to long-term planning and prioritizing their efforts for 2020. For most, it’s likely that the new year will bring with it new technology and innovation. But, with all the developments in technology and changes in process and workflow these days, it can be difficult to translate innovation into real improvements for your organization.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

National Archives Records Express
DECEMBER 17, 2019
On December 11, 2019, the Archivist of the United States approved a request for disposition authority from the U.S. Immigration and Customs Enforcement (ICE) for Detainee Records (schedule DAA-0567-2015-0013). This schedule was originally proposed to NARA on October 26, 2015. NARA published notice of the pending schedule in the Federal Register on July 14, 2017.
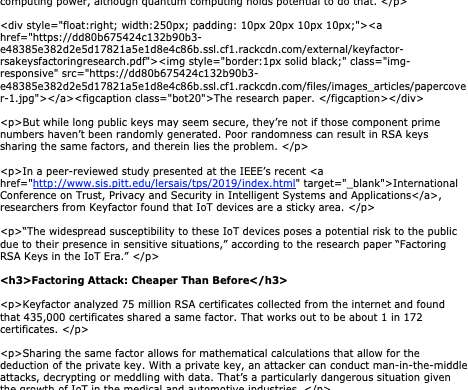
Data Breach Today
DECEMBER 17, 2019
Weakness Lies in Devices Without Quality Entropy Sources IoT devices are generating duplicate prime numbers while generating RSA keys, putting them at risk of a factoring attack, according to new research, which shows such an attack could be done at scale and at a low computing cost.
Security Affairs
DECEMBER 17, 2019
TP-Link has addressed a critical vulnerability impacting some TP-Link Archer routers that could allow attackers to login without passwords. TP-Link addressed a critical zero-day vulnerability ( CVE-2017-7405 ) in its TP-Link Archer routers that could be exploited by attackers to remotely take their control over LAN via a Telnet connection without authentication. “This is a zero-day flaw that was not previously reported and can affect both home and business environments.” explained

Data Breach Today
DECEMBER 17, 2019
Enhanced Authentication Could Help Beef Up Security of the Supply Chain To help enhance security, Firefox extension developers will be required to set up their accounts to support two-factor authentication beginning early next year, Mozilla, the open source community that supports the browser, has announced.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
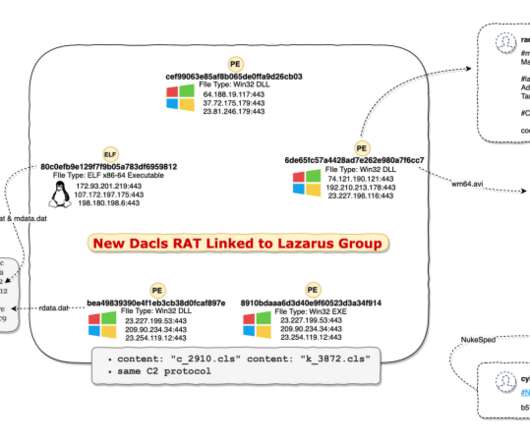
Security Affairs
DECEMBER 17, 2019
Researchers spotted a new Remote Access Trojan (RAT), dubbed Dacls, that was used by the Lazarus APT group to target both Windows and Linux devices. Experts at Qihoo 360 Netlab revealed that the North-Korea Lazarus APT group used a new Remote Access Trojan (RAT), dubbed Dacls, to target both Windows and Linux devices. The activity of the Lazarus APT group (aka HIDDEN COBRA ) surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks.

Data Breach Today
DECEMBER 17, 2019
Cybercrime Gang's 'Naming and Shaming' Ties to Pressure Victims Into Paying The gang behind Maze ransomware has begun publicly identifying its victims and listing data that it exfiltrated from systems before leaving them crypto-locked. The intent is clear: By naming and shaming victims, the Maze gang is trying to compel them to pay.

Adam Levin
DECEMBER 17, 2019
New Orleans has declared a state of emergency following a ransomware attack. The city government has effectively been offline since December 13 when employees were instructed to turn off all computers and disconnect them from WiFi networks following reports of suspicious network activity. . “The city asks residents and vendors for their patience and understanding as our Information Technology team works to restore all operations to normal,” said New Orleans mayor LaToya Cantrell.

Data Breach Today
DECEMBER 17, 2019
Improving the security of diverse medical devices is a major challenge for a variety of reasons, according to security leaders at two device manufacturers, who spell out the key issues in this interview.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Dark Reading
DECEMBER 17, 2019
Protecting the places where application services meet is critical for protecting enterprise IT. Here's what security pros need to know about "the invisible glue" that keeps apps talking to each other.

WIRED Threat Level
DECEMBER 17, 2019
By exploiting flaws in popular video conferencing hardware from DTEN, attackers can monitor audio, capture slides—and take full control of devices.
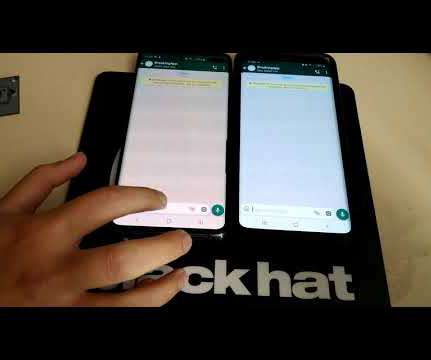
Security Affairs
DECEMBER 17, 2019
WhatsApp fixed a severe bug that could have allowed a malicious group member to crash the messaging app for all members of the same group. WhatsApp addressed a severe vulnerability that could have allowed a malicious group member to crash the messaging app for all members of the same group. An attacker could trigger the vulnerability by sending a maliciously crafted message to a targeted group, the message caused the app entering a loop that crashed the devices.

Micro Focus
DECEMBER 17, 2019
Whether driven by the need to switch platforms and update older systems, or as part of a broader, strategic IT initiative, ERP and CRM systems are a significant part of the IT landscape being targeted in many organizations today. However, the approach is not without considerable business risk. I recommend the careful consideration of a. View Article.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Security Affairs
DECEMBER 17, 2019
vpnMentor researchers discovered an unsecured server belonging to the Chinese e-store LightInTheBox.com containing 1.3TB of web server logs. Infosec researchers have uncovered an unsecured Elasticsearch database containing 1.3TB of web server log entries held by Chinese e-commerce website LightInTheBox.com. LightInTheBox is a Chinese online retailer trading on the New York Stock Exchange, most of its customers are in North America and Europe.

Threatpost
DECEMBER 17, 2019
Researchers say that Amazon and Google need to focus on weeding out malicious skills from the getgo, rather than after they are already live.

IBM Big Data Hub
DECEMBER 17, 2019
When planning for a day of business, how do you calculate the numerous factors that may affect your bottom-line revenue? For Serco, a company which operates a bike-sharing service throughout London, the answer was in their data.

Threatpost
DECEMBER 17, 2019
The Epilepsy Foundation has filed a criminal complaint against undisclosed Twitter users who users its Twitter feed to post seizure-inducing content.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Zapproved
DECEMBER 17, 2019
Zapproved, the leading ediscovery software provider for managing corporate litigation, today announced that Rekha Shenoy has joined the company as Chief Product Officer. The post Welcome Chief Product Officer Rekha Shenoy! appeared first on Zapproved.

Information Governance Perspectives
DECEMBER 17, 2019
The Federal Trade Commission finalized a settlement with an email management company that allegedly deceived some consumers about how it accesses and uses their email. The FTC alleged that Unrollme Inc., which helps users unsubscribe from unwanted emails or consolidate their email subscriptions, falsely told consumers that it would not “touch” their personal emails in order Continue reading.

WIRED Threat Level
DECEMBER 17, 2019
The flaw would have given attackers an avenue for crashing the app—every time a user opened an infected group thread.

Jamf
DECEMBER 17, 2019
This JNUC 2019 session focused on how Apple's accessibility features can level the playing field for people with diverse needs.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Schneier on Security
DECEMBER 17, 2019
New details : At the CyberwarCon conference in Arlington, Virginia, on Thursday, Microsoft security researcher Ned Moran plans to present new findings from the company's threat intelligence group that show a shift in the activity of the Iranian hacker group APT33, also known by the names Holmium, Refined Kitten, or Elfin. Microsoft has watched the group carry out so-called password-spraying attacks over the past year that try just a few common passwords across user accounts at tens of thousands

Information Management Resources
DECEMBER 17, 2019
Top analytics trends in 2020 will include the rise of a new analytics stack, a more diagnostic approach to analysis, a demand for more useful facts, and the emergence of a new role - the operational analyst.

Jamf
DECEMBER 17, 2019
Learn how to customize Swift Playgrounds by applying settings remotely with Jamf Pro or Jamf School.
Let's personalize your content