Train Your Team to Ensure You Achieve ISO 27001 Certification
IT Governance
OCTOBER 26, 2022
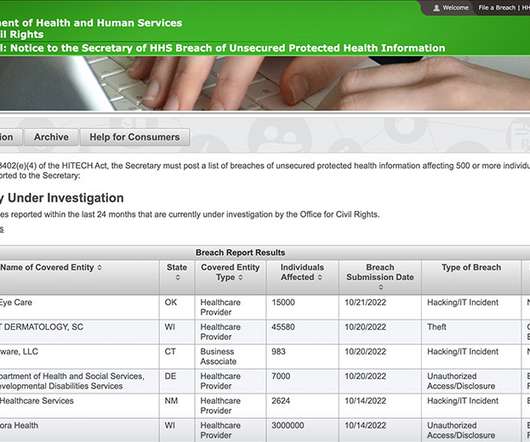
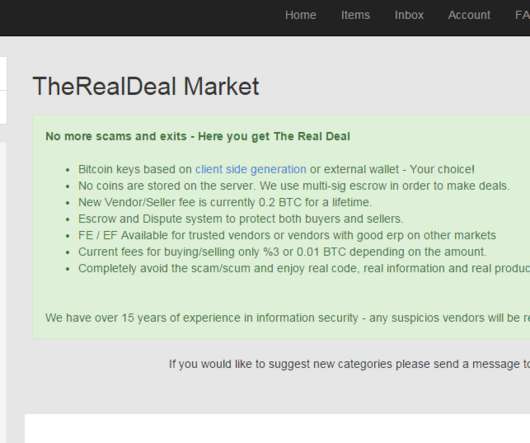
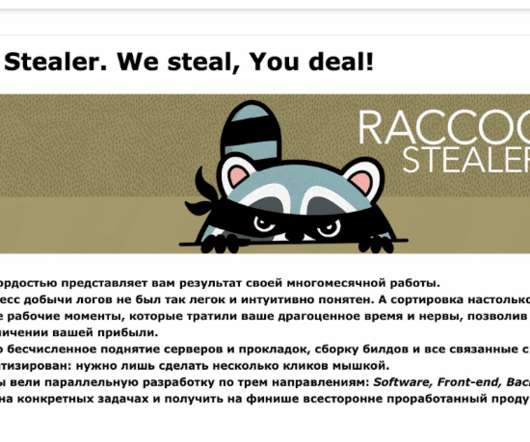
Implementing an ISO 27001-compliant ISMS (information security management system) can seem complex, and it’s often difficult to know how the Standard’s specifications should be applied to your organisation. Failure to understand or comply with the requirements of the Standard could jeopardise your implementation project. This will likely mean you fail the certification audit, potentially costing your organisation dearly.








































Let's personalize your content