China-linked APT31 targets Russia for the first time
Security Affairs
AUGUST 4, 2021
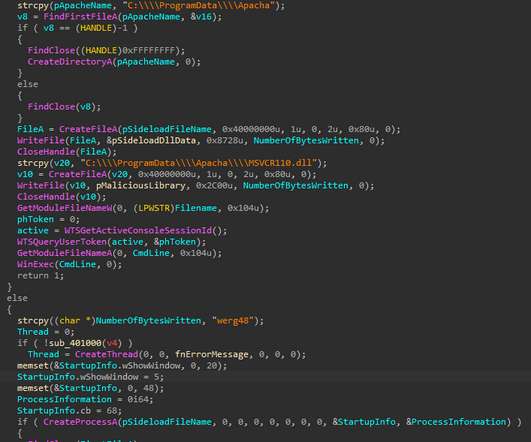
China-linked APT31 group employed a new strain of malware in attacks aimed at entities in Mongolia, Belarus, Canada, the US, and Russia. Researchers from Positive Technologies reported that China-linked APT31 group has been using a new piece of malware in a recent wave of attacks targeting Mongolia, Belarus, Canada, the United States, and Russia. Experts found many similarities between the malware and the DropboxAES RAT that was first spotted by researchers at Secureworks and that was previously









































Let's personalize your content