FCC Finalizes Plan to Rip and Replace Chinese Telecom Gear
Data Breach Today
JULY 14, 2021
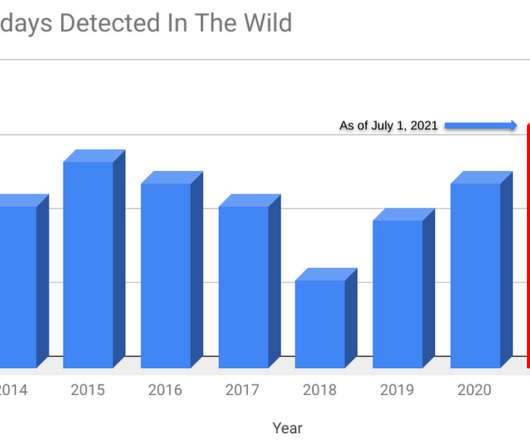
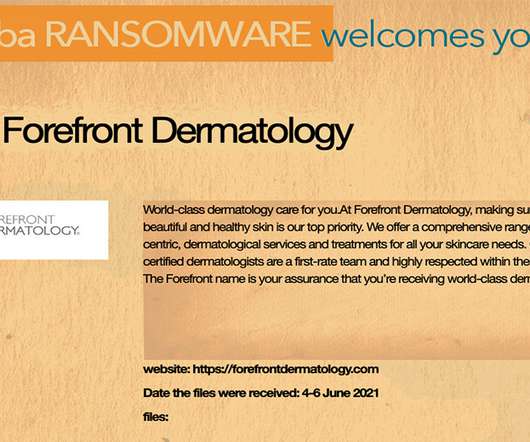
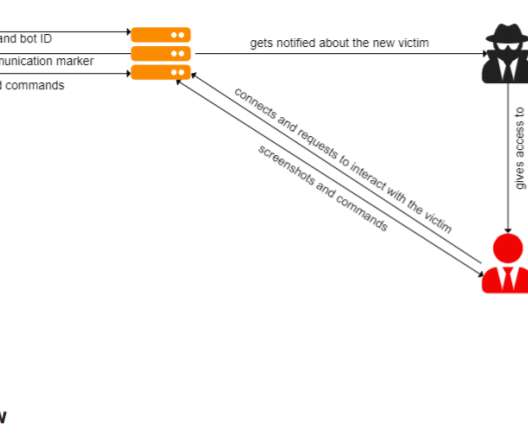
Commission Says Huawei, ZTE Are National Security Threats The FCC has finalized a $1.9 billion plan that will help smaller, rural telecommunications carriers pay to rip and replace technology from the Chinese firms Huawei and ZTE. The commission says using the gear poses a threat to U.S. national security.



































Let's personalize your content