Why Does EternalBlue-Targeting WannaCry Remain at Large?
Data Breach Today
MARCH 9, 2021
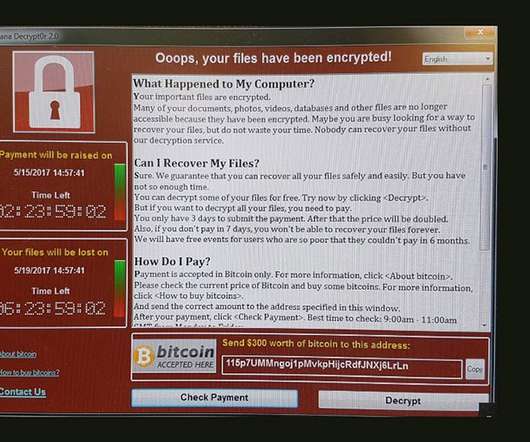
'The Most Widely Successful Wormable Malware Becomes Almost a Permanent Hangover' Nearly four years after the WannaCry ransomware hit the world, targeting the EternalBlue vulnerability in Microsoft SMB version 1, security firms say the malware continues to be a top threat detected in the wild by endpoint security products. Why won't WannaCry just die?







































Let's personalize your content