Malicious npm package ‘fallguys’ removed from the official repository
Security Affairs
AUGUST 30, 2020
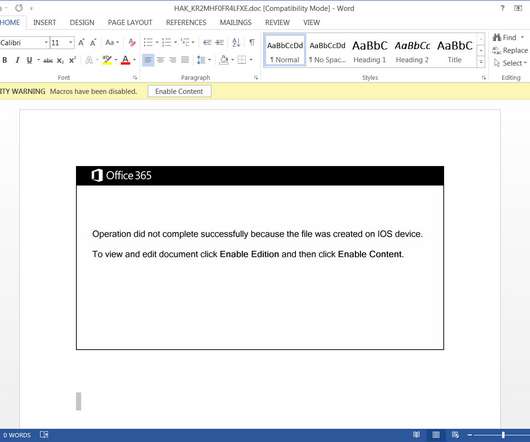
The npm security team removed a malicious JavaScript library from the npm repository that was designed to steal sensitive files from the victims. The npm security team has removed the JavaScript library “ fallguys ” from the npm portal because it was containing a malicious code used to steal sensitive files from an infected users’ browser and Discord application.














Let's personalize your content